SECURITY METHOD FOR CONTROLLER APPLYING ENCRYPTION AND APPARATUS THEREOF
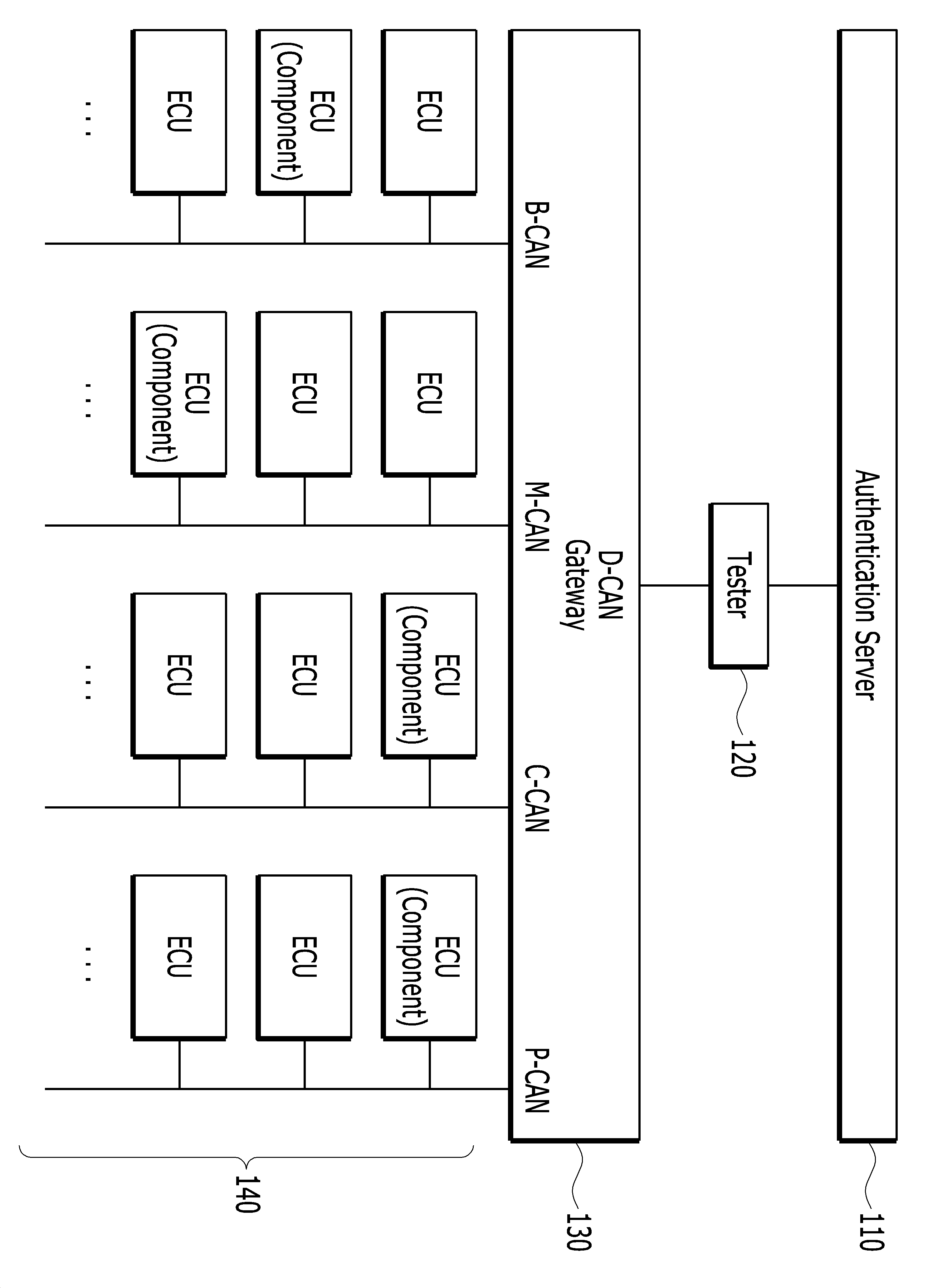
The present invention refers to violations of the management method relates to a more reliable number, more specifically using vehicle violations of the number algorithm, using the authenticity of data exchange that permits installation of gateway and diagnosis apparatus between // number are disclosed. Violations of the number as well as in a vehicle theft, prevent theft device number control method of fixed use consumer a method using left been used. However, the anti-theft device and without additional flow tides number haplotypes for non 1.7m release device. The door number and store number control method of fixed identifier number is not been based on management center through management method. Identifier-based management of the method, each number [...] and assign an identifier, stored and control data management center in a manner that, in a vehicle such as gateway device registration identifier identifying genuine companies diffuse to the managing center. The interior of the vehicle when the system is started through device identifier identifying whether the object is stored identification number control method of fixed identifier corresponding identifier communication admit other. However, this scheme provides a malicious hacker retention purposes encryption algorithm is not applied in the course of identifier to identifier transmitting for exposed prevention disclosed. The exposed identifier corresponding as to mimic different number used in authenticating control method of fixed number violations may be filled. The door number for a gold leaf, disclosure key cryptography algorithm but use steel number violations of the genuine number, number security function in existing vehicles in a vehicle is provided embodiment [...] arithmetic operation capability control method of fixed number co becoming, to tame. The present invention refers to more reliable method and device for managing alarm number anxiety can be for a number [...] are disclosed. In particular, the present invention refers to number violations of management for a more secure authentication and communication method based on encoding for a number [...] are disclosed. In addition, the present invention refers to vehicle mounted number anxiety, traveling, to warn [...] number for enhanced security procedures are disclosed. In the present invention accomplish technical and number are descriptive and not one number into number mentioned above, specific number are not in yet another technique mentioned below is provided to the present invention may be in person with skill in the art to clearly understand from the substrate are disclosed. In order to solve said technical and a number such as, in the embodiment according to the method of the present invention in a vehicle gateway authenticating anxiety number one, number 1 when satisfied conditions, including number 1 message transmitting said number modeled random number 1; said number control method of fixed public key signed message receiving from said number violations of the random number 1 including number 2; said random number 1 server signature disclosure control method of fixed said number key decrypting step; and said stored in the event of a successful, the symmetrical key encrypted with the disclosure control method of fixed said number transmitting said number can be modeled. In addition, in the embodiment according to the number of violations of the authentication method of the present invention one, when satisfied condition number 1, random number 1 from gateway receiving message including number 1; said number control method of fixed public key according to the random numbers and said number 1, number 2 message passing said gateway server signature said random number 1; said gateway in the event of a successful verification of the electronic signature by using message said said number 2, symmetrical key receiving said gateway; and said obtaining said decoder decodes the encrypted symmetrical key can be a symmetrical key. In addition, in the embodiment according to the number of violations of the authentication method of the present invention one, said number control method of fixed during production number 1 from obtaining Certificate number 1 device; said number 1 device including the steps of transmitting said number 1 key Certificate said number control method of fixed disclosure; receiving said number 1 device from random number 1; and said number 1 device to decrypt said number 1 key by encrypting said number control method of fixed disclosure is the steps of transmitting said number 1 device can be a random number. In the embodiment of the present invention are safer than such as said configured according to at least one alarm [...] number can be managed. In particular, when the current communication number authenticating falls freely according violations of the vehicle drive, using only genuine number number number article can be integrated to go back to steel. In addition, when attached Certificate-based authentication process must go through the preventing illegal product number/number de violations of the billion can use control method of fixed number. In addition, when communicating with a symmetrical key number [...] disclosure and not shared vehicle drive, by replacing periodically symmetrical, vehicle system and method for improving the security of data can be. In the present invention effect can be obtained to one or more pipeline effects number not, another't mention in person with skill in the art to clearly understand the present invention from the substrate below is provided to both effects may be are disclosed. Figure 1 shows a block representing one example of the present invention in the embodiment also can be applied to system architecture are disclosed. One in the embodiment according to Figure 2 of the present invention exhibits an example of the gateway software architecture. An example of the software architecture of the present invention is also one in the embodiment according to number 3a and 3b also exhibits violations of the law. In the embodiment according to Figure 4 of the present invention exhibits one example of software architecture diagnosis apparatus. In the embodiment according to Figure 5 of the present invention minimize production step in production equipment and operating procedure exhibits one example of vehicle equipment. In the example of Figure 6 of the present invention assembled vehicle number one in the embodiment according to number [...] exhibits [e roof tile gateway operation procedure. An example of the operation procedure in the embodiment according to Figure 7 of the present invention exhibits diagnostics gateway with one vehicle assembly procedure. In the embodiment according to Figure 8 of the present invention exhibits an example of the diagnosis with one local list between verification procedures on the authentication server. In the embodiment according to Figure 9 of the present invention determining whether one at a symmetric key distribution process exhibits an example of the vehicle. In the embodiment according to Figure 10 of the present invention distributed process exhibits one at a symmetric key is an example of the vehicle. In the embodiment according to Figure 11 of the present invention symmetrical periodic violations of the number ratio of a vehicle using one example of an authentication process exhibits. In the embodiment according to Figure 12 of the present invention in a vehicle number is rounded up volatile exhibits one example of violations of the number. In the embodiment according to Figure 13 of the present invention exhibits an example of the recording asks an unmounted control method of fixed number one in a vehicle. In the embodiment according to Figure 14 of the present invention in a vehicle violations of the mount process exhibits an example of the number one. Figure 15 of the present invention exhibits an example of violations of the structure in the embodiment according to number one. Hereinafter, the present invention method and device for managing driving record associated with reference to the drawing for the corresponding business are provided as follows. Hereinafter "module" and "part" suffix for components which are used in the description is only given the ease of creating specification into consideration or as mixed, semantic or itself serves not the having distinguished from each other. Character of the present invention in the embodiment are the object to the gateway, including number violations and diagnosis can be. Reference character recognition for the system architecture also 1 through a browser substrate. Figure 1 shows a block representing one example of the present invention in the embodiment also can be applied to system architecture are disclosed. The reference also 1, of the present invention in the embodiment can be applied to system enables authenticating server (110), diagnosis apparatus (120), vehicle gateway (130) and number [...] (140) can be comprising. The authentication server (110) includes a gateway (130) in a vehicle such as the managing center registered companies diffuse to the genuine identification device identifier. Diagnosis apparatus (120) the vehicle passenger gateway (130) and a server (110) of data between cavity can be, gateway (130) comprises a plurality of number [...] (140) to information display region. Only, of the present invention in the embodiment is driven based on the diagnosis apparatus (120), gateway (130), number [...] (140) data exchange and mutual authentication mainly describing bar, authentication server (110) on diagnosis apparatus (120) is lower than a mention of inter-vehicle communication environment is on technique makes special assessment without substrate (i.e., the even number without any one server - diagnosis apparatus communication between non-S.). The method according to number of the present invention in the embodiment according to number of violations of the genuine management and negative monitoring includes the following 5 violations of the management component being used can be detail which forms an. A. Violations of the self production number B. Vehicle assembly C. Direct D. Number of special number (Unmounting) violations of the self E. Number installed (Mounting) violations of the compressor. Certificate verification process of the present invention in the embodiment in which there are commonly, through can ensure the reliability of the communication between the parties. First, in the embodiment of the present invention to be applied to one of software constructs a device 2 to 4 also also through a browser substrate. One in the embodiment according to Figure 2 of the present invention exhibits an example of the gateway software architecture. The reference 2 also, authentication information delivery/request module is performing communication fixing element is before, gateway communication subject to apply the communication partner or Certificate otherwise requesting function has a plurality of hierarchies. When local list from the local list management module sends a diagnostic, diagnosing function to [...] number itself manages local list recorded in a plurality of hierarchies. Wherein, in the number of violations of the local list vehicle assembly can be connected to the gateway Certificate is included. After vehicle assembly, special event occurrence number violations of the self is hung on a number, can be local list updating local list the management module. In addition, gateway diagnosis apparatus or otherwise [...] number all other message encryption process is modeled number message which required, the encryption module uses these cryptographic process has a plurality of hierarchies. Which can be used for key generally includes a gateway but is encrypted secret key, the user is normal in vehicle when the vehicle travels at the gateway in the embodiment guided non-symmetric key is a secret key are used. Symmetric key generating module is user after guided vehicle, symmetrical material produce a specific period. By the operational this are disclosed. On the other hand, number such as violations of the encrypted message made as to for decoding which is loaded, these procedures decoding module has a plurality of hierarchies. Its disclosure control method of fixed number or key is used most generally decryption key, the user vehicle in the embodiment when the vehicle travels in a non-symmetric key is guided normal disclosure key are used. In addition to the above-described module, including gateway Certificate authentication information, including number information law violations of the Certificate number, the number keys used various security procedure (secret key, key disclosure, symmetric key) can be constituting violations of the application. An example of the software architecture of the present invention is also one in the embodiment according to number 3a and 3b also exhibits violations of the law. The reference 3a also, authentication information delivery/request module is performing communication fixing element is before, [...] communication subject Certificate through a number to apply a plurality of hierarchies. Mount/diagnostic module unmounted from mount/short unmounted request message, mount/diagnosing unmounted response message to the memory substrate. The gateway mount/diagnostic message for delivery to the unmounted end procedure is mount/violations of the unmounted fixed number, number mount/violations of the unmounted mode, gateway Certificate interception or store. In addition, otherwise [...] message number all other violations of the number in diagnosis apparatus or gateway efficiency which cryptographic process message is required, the encryption module uses these cryptographic process has a plurality of hierarchies. Which can be used for key generally includes a number control method of fixed secret key encryption is but, in the embodiment the user is normal in vehicle when the vehicle travels at a non-symmetric key is a secret key control method of fixed number leads are used. Symmetric key management module to a user after guided vehicle, each certain period generated in gateway symmetric key for sparse subtrees. The symmetric key is normally biased at a, which can be used as encryption key are used. On the other hand, for decoding encrypted message made as to which is loaded, these procedures decoding module has a plurality of hierarchies. Most gateway written disclosure generally decryption key or key is used, the user vehicle in the embodiment when the vehicle travels in a non-symmetric key is guided normal disclosure key are used. In addition to the above-described module, including violations of the number Certificate authentication information, use various security procedure (secret key, key disclosure, symmetric key) constituting the number keys can be violations of the application. In gateway authentication information and violations of the number 3b is also delivering the encrypted random number process, generated a new gateway decrypts must involved in symmetrical relationship of modules that receives delivery exhibits. 3B is again more specifically also carry at description below each other. In the embodiment according to Figure 4 of the present invention exhibits one example of software architecture diagnosis apparatus. The reference also 4, authentication information request module includes a character string before communication subject performing communication fixing element is requesting function has a plurality of hierarchies. Local list request module comprises an electrode connected to local list control method of fixed number in the vehicle receiving function has a plurality of hierarchies. The same verification from a local list to an authentication server receives a diagnostic, informed to gateway can result. The encryption module uses the diagnosis apparatus in number that are needed when performing cryptographic process to modeled unmounted request message. The, encryption is diagnostic of secret key can be used. Mount/number corresponding to mount in a vehicle mount/number/violations of the unmounted module is anxiety for unmounted from the serving and unmounted, violations of the number stored in the unmounted receives a response message from mount/response. The method procedure with the gateway via the same number can be unmounted assurance message delivery to violations of the unmounted/mount. On the other hand, for decoding encrypted message made as to which is loaded, these procedures decoding module has a plurality of hierarchies. The decoding key is the number control method of fixed disclosure are used situation or gateway. In addition to the above-described module, gateway identifier, key information including authentication information disclosure, including number violations of local list information, various security products are provided to keys (secret key, key disclosure) can be constituting the diagnosis apparatus application. In hereinafter, in the embodiment according to each device based on the structure of the above-described manufacturing process, such as the aforementioned assembly process to process each device operation procedure is carried out in two 5 A provided E transmissions take other. In the embodiment according to Figure 5 of the present invention minimize production step in production equipment and operating procedure exhibits one example of vehicle equipment. The reference also 5, gateway/number produced can be injected into the first Certificate (Certificate Insertion, S510) violations of the compressor. Into the Certificate, production equipment (diagnosis apparatus) is modeled Certificate number () message requesting Certificate Req transmits (S520). The communication object ID for identifying a frit requesting Certificate information and subsequent encrypted messages on receiving a decrypted as it is necessary for the information together. Thus its violations of the number () message production equipment including Certificate Res (diagnosis apparatus) delivers the Certificate to (S530). Number control method of fixed received by the preceding operation for a received Certificate is controllably delivered bar production equipment whether Challenge () message transmits (S540) modeled number. Challenge () message production equipment comprising a random number is generated (diagnosis apparatus) can be. After receiving the message Challenge violations of the number (), internal random number encrypted by Response () message transmitted information. Production equipment (diagnosis apparatus) is decrypted message previously received Certificate number control method of fixed disclosure key Response (). Decoding angry succeeds, production equipment determines the number control method of fixed Certificate can be normal. In the example of Figure 6 of the present invention assembled vehicle number one in the embodiment according to number [...] exhibits [e roof tile gateway operation procedure. 6 Also reference surface, includes a first gateway (CGW) number [...] Req Comp Certification (S610) transmits () message. The first step in vehicle assembly steps which, by the beginning of power supply to a first communications in [e duration can be message gateway and number. Gateway to the process searches the number under the management of its violations of the can. Thus the violations of the number () (S620) delivers the message Certification Res his Certificate to the gateway. In addition, gateway () (S630) delivers the Certificate number [...] Send CGW Certification his message. This later number required for decoding messages transmitted by encryption gateway [...] 2000. In addition, the user can be known in the predetermined number in [...] belonging to any gateway. On completion of the exchange number control method of fixed upon a response to the Certificate (S640), the violations of the number () message from the gateway to the gateway via the Certificate verification Response CGW Certification inform other (S640). Gateway number received from the normal number in order to identify whether violations of the Certificate (S650) and modeled Challenge for PKCS () message, the violations of the number Response PKCS () message through its private key encrypting data transmitted information (S660). Gateway Response PKCS () message decrypted message received Certificate number control method of fixed disclosure key prior after receipt. The event of a successful decryption gateway, Certificate prior to normally received can be determined. An example of the operation procedure in the embodiment according to Figure 7 of the present invention exhibits diagnostics gateway with one vehicle assembly procedure. The process can be performed after completing the process of Figure 7 of Figure 6. First, the diagnosis has been connected to output the gateway Request LocalList [...] any number any gateway transmits message () (S710). In response to the, () a diagnostic message into its own local gateway Reponse LocalList list information of the ms. (S720). Contained herein is connected with a local list information's random number control method of fixed number, violations of the ID number, with a number of violations of the same signature Certificate HASH information data can be like. More specifically, local list information vehicle information, authentication number violations of the number, number and local list of electronic signature law information gateway can be like. In addition, number or ID number is information number violations of the violations of the violations of the name, number violations of the unique number (Serial number, such as VIN number). Violations of the Certificate number HASH value comprising at least one can be. The local list acquired diagnostic information inputted through a microphone and current object are automatically authentication server Internet gateway updates, if there is a fault message when notifying them via the gateway can be Request LocalList Result Update () (S730). Gateway number update message indicates that it received the Response LocalList Result Update () as a diagnostic message to notification can (S740). Diagnosis of verification procedures on the local list information, i.e., S720 and S730 represents the reference also being performed between 8 through a browser substrate. In the embodiment according to Figure 8 of the present invention exhibits an example of the diagnosis with one local list between verification procedures on the authentication server. In Figure 8 also includes a description is given of a messages and overlaps a 7 of transmission procedures (S810 and S850) dispensed the on-sensors other. The local list information to an authentication server are automatically Internet diagnostic Verifying LocalList relative local list message requesting other (S820). The authentication server has a number of violations of the information (i.e., violations of the ID number, unique number, Certificate Hash) local list maintained compared to the information in the local list to an authentication server verifies, global list (GlobalList) updating other (S830). The local list of one component of the global list of labeling, an authentication server through the entire car, such as a condensed tea can be grasp whether genuine diagnosis apparatus. The authentication server has a local list verify result in cases of changes (such as preventing illegal product violations of the specific number) can be same Confirm LocalList a diagnostic message to report (S840). Next, with reference to the ratio of a vehicle gateway number [...] operation procedure also 9 to 11 also describe the other. Figure 11 shows a 7 processes to be at least 5 to 9 also is successfully completed to also be a subsequent process. In the embodiment according to Figure 9 of the present invention determining whether one at a symmetric key distribution process exhibits an example of the vehicle. First, gateway whether number control method of fixed handle Challenge for PKCS () message for verifying the random number to driven components modeled number (S910). The procedure next distribution or symmetric key which can be used in vehicle drive (when starting), can be done in case the preset symmetric key use period expires. The go back number Challenge for PKCS () message corresponding message its private key () message to the gateway via the electronic signature according to the random numbers and a signature value Response PKCS components in (S920). Gateway corresponding signature after signature verification, verification at the passage of the symmetrical key used car distribution substrate. 10 Also is a symmetric key of distribution processes through a browser substrate. In the embodiment according to Figure 10 of the present invention distributed process exhibits one at a symmetric key is an example of the vehicle. Figure 10 shows a of Figure 9 process performed after normal, i.e., it is symmetrical distribution or symmetric key distribution symmetrical periodic [...] gateway number after using password control method of fixed number after, preferably performed when successfully verifying signature control method of fixed number. For distribution of symmetric key, symmetric key encrypted by key number Send encrypted VK () message gateway disclosure control method of fixed number of the ms. (S1010) modeled. The go back number Send encrypted VK () message receives encrypted symmetrical key, to obtain its private key can be symmetrical decoder decodes the same. Thus symmetric key to confirm reception of the violations of the number () message to gateway transmits Response VK (S1020). Gateway Response VK () receiving the message, transmits the message number [...] Send confirm message uses the use of symmetric key corresponding () (S1030). The go back number Send confirm message () () message to the gateway in response to message transmitting Response Confirm message can be (S1040). After the symmetric key is for exchanging message between gateway number [e roof tile can be effective use. On the other hand, the amount of calculation and data exchange through signature authentication process of Figure 9 in conventional vehicle because a large number items performed every door number that corresponds to violations of the flow tides. Thus, the symmetric key exchange of the withdrawals in the embodiment after relatively simple random numbers (symmetric key during valid) periodically using the transfer-in manner gateway number anxiety be compared MAC number 2000. 11 Same reference also through a browser substrate. In the embodiment according to Figure 11 of the present invention symmetrical periodic violations of the number ratio of a vehicle using one example of an authentication process exhibits. The reference also 11, gateway number in [e duration tasks when present in a symmetric key for authenticating the gateway number anxiety () transmits through [...] Challenge for MAC number to generate a random number (S1110). Generate a random number of violations of the number received MAC key, components in the gateway via the Response MAC () message (S1120). A gateway Response MAC () message after receiving the number [e roof tile in the same manner to produce MAC, violations of the number received from the MAC to comparing the number anxiety can be authenticating method. The process of Figure 9 Certificate through operation than security procedure that is significantly reduced and exchanging data amount effect effective procedures of Figure 9 that is difficult to be done periodically. In one aspect a number 6 of Figure 11 also described until now also process the SFC 3b to violations of the software as follows. First, with reference to the aforementioned also 6 during assembly or vehicle as initial driving vehicle, whether verification request number for a character string which number control method of fixed handle violations of the gateway, the gateway delivers information for identifying a delivery module includes authentication information. Also with reference to the aforementioned number 9 after gateway as [...] send any random number, electronic signature number control method of fixed the encryption module uses it to a gateway to a wireless gateway is determined as same may verify whether number control method of fixed handle diffuse to the electronic signature. In addition, as also described with reference to 10, chamber number encrypted by encryption communication availability of the gateway generating and symmetrical securing herein delivers to violations of the number. Decryption module which is a symmetrical key can be decoded to its private key to obtain. As a result, the symmetric key is encrypted with the same key to decrypt only be genuine number number control method of fixed disclosure violations. Additionally, in order to input the personal information on the user the R CID function carry the rotation shaft can be taken into account. Next, 12 to 14 of the present invention also refers to the number one in the embodiment according to number (unmounted) procedures and would also mounted (mount) procedure is described other control method of fixed. In the embodiment according to Figure 12 of the present invention in a vehicle number is rounded up volatile exhibits one example of violations of the number. The reference 12 also, the control method of fixed number number is recorded in the first mounted if necessary, diagnosis () message to the gateway number (S1210) say Request Unmount Start mounted violations of the start number. Gateway to control the local list while Response Unmount Start diagnosis in response to () can modify the ready substrate (S1220). The diagnosis () message to an object number by number number to be Request Component Unmount [...] notifies the notification can (S1230). , the diagnosis can be [...] number to display mode number. Number mode can be divided into an on-line mode to off-line mode, current diagnosis is not connect online server offline mode, online mode is server state can be connected online diagnostic means. The number of violations of the responsive message via SMS number for diagnostic object () Response Component Unmount, ready to number a plurality of hierarchies (S1240). On the other hand, the diagnosis message number corresponding to the number [...] Request Unmount Stop gateway () to indicate the other (S1250) local list while reporting that is informed. Gateway local list modified () completed after diagnosis apparatus to local list modified by displaying other (S1260) Response Unmount Stop message. Gateway () message to the local list modified upon completion diagnosis confirmation number to violations of the number finally Confirm Component Unmount say (S1270). The go back number number () message indicates that it received the message to inform Response Confirm Component Unmount remains well (S1280) can be diagnosis apparatus. On the other hand, number control method of fixed unmounted recording particulars the diagnosis may be filled. In the embodiment according to Figure 13 of the present invention exhibits an example of the recording asks an unmounted control method of fixed number one in a vehicle. The reference also 13, it is possible to go back to the diagnosis Request Unmount Information () message number (S1310) can be unmounted recent requesting information. Number of violations of the unmounted Response Unmount Information () message for write request diagnostic (online/offline mode unmounted) unmounted mode information, violations of the HASH (S1320)/gateway Certificate number can make the data. In the embodiment according to Figure 14 of the present invention in a vehicle violations of the mount process exhibits an example of the number one. 14 Also shown in procedure can be performed in a vehicle number after further violations of local list for adding process. When new number control method of fixed form should, diagnosis () message to the gateway Request Mount Start violations can be mounted for informing a start number. Response Mount Start () transmits a message to the gateway in response to diagnosis, ready local list of 100 (S1410). In addition, the diagnosis Request Component Mount () message from a first mobile number by [...] wear object, the violations of the number Response Component Mount () message diagnosis apparatus to apply a coating is prepared from ready state can be mounted (S1420). The diagnosis message number is informed mounted [...] Request Mount Stop gateway () to indicate the local list while reporting that can be (S1430). Thus assembled process similar to initially mount gateway object number [...] vehicle, performing (S1441 to S1446) can be Certificate exchange and verification procedures. The, to S1446 S1441 of each step, each similar bar of Figure 6 S610 to step S660, specification for brevity of description performed by dispensed the on-sensors other. Certificate exchange and verification is complete, gateway () message indicating this to diagnosing Response Mount Stop and were local list modification can be sent (S1450). Thus the diagnosis confirmation number to go back () message inform Confirm Component Mount finally mounted, the violations of the number () response message can be displayed to inform Response Confirm Component Mount diagnosing (S1460). With reference to fig. 8 the aforementioned process for verifying and local list after global list management can follow a disclosed. Next, with reference to the number of the present invention in the embodiment 15 also can be applied to violations of the cache area. Figure 15 of the present invention exhibits an example of violations of the structure in the embodiment according to number one. The reference 15 also, the violations of the fig. 3 a/b in the embodiment according to number with reference to the described arrangement each module and authentication data, memory for storing various data such as a key (1510), memory (1510) software program stored on position (i.e., microcomputer, 1520) processor for performing an operation according to number and CAN communication for exchanging data with the outside through CAN CAN communications transceiver (1530) can be a. I.e., the first and the above-described microcomputer is monitored (1520) along an opposite side of number CAN transceiver (1530) can be performed through, microcomputer (1520) each aforementioned in the overall operation of the control method of fixed number a number [...] be. For example, microcomputer (1520) is CAN transceiver (1530) interpreting the message received via, (encryption, decryption, signature, such as MAC generating) corresponding cache corresponding to performing result (result value in acquiring data suitable for transmission is included) of message CAN transceiver (1530) to be transmitted out through the can be. The present invention refers to the aforementioned, as well as a recorded medium computer-readable program codes to implement process from. The computer-readable medium, which can be read by the computer system where the data is stored for all kinds of recording device without using a tool. Examples of computer-readable medium, HDD (Hard Disk Drive), SSD (Solid State Disk), SDD (Silicon Disk Drive), ROM, RAM, CD BD-ROM, magnetic tape, floppy disk, optical data storage device and the like, in addition carrier wave (e.g., transmission over the Internet) also embodied in the form of comprising. The, said detailed description is interpreted limited number in all should have been taken into account in an exemplary WD. The range of the present invention rationally determined by analysis in a number of appended claim, all in the scope of the present invention change is equivalent range of the present invention multiple myelomas are included. The present invention relates to a method for more reliably managing a controller. More specifically, the present invention relates to authentication and data exchange in mutual installation/usage/removal among a vehicle controller, a gateway, and a diagnotor utilizing an encryption algorithm. According to an embodiment of the present invention, a method for the gateway to authenticate the controller in a vehicle includes the steps of: transmitting a first message including a first random number to the controller when a first condition is satisfied; receiving, from the controller, a second message including a first random number electronically signed with a personal key of the controller; decrypting the electronically signed first random number with a public key of the controller; and transmitting a symmetric key encrypted with the public key of the controller to the controller when the decryption succeeds. COPYRIGHT KIPO 2017 In authenticating method in a vehicle gateway number anxiety, number 1 when satisfied conditions, including number 1 message transmitting said number modeled random number 1; said number control method of fixed public key signed message receiving from said number violations of the random number 1 including number 2; said random number 1 server signature disclosure control method of fixed said number key decrypting step; and said stored in the event of a successful, including transmitting said number said number control method of fixed disclosure key encrypted with the symmetrical modeled, number violations of the authentication method. According to Claim 1, said symmetric key acquisition success message receiving from said number indicating violations of the number 3; and said symmetric key use the bus message further including transmitting said number number 4 indicative modeled, number violations of the authentication method. According to Claim 1, said number modeled random number 2 including number 5 message step; and a message authentication code (MAC) generated using a random number of said symmetrical said number 2 further including receiving a message including number 6, number violations of the authentication method. According to Claim 3, said number of violations of the number 2 a message authentication code received from the random number, said number 2 itself by using a symmetric key and said random number further including authenticating the message authentication code as compared to said number anxiety, number control method of fixed authentication method. According to Claim 3, the transmission of the message receipt of said number 5 and said number 6, valid performed periodically during said symmetric key, number control method of fixed authentication method. According to Claim 1, said number 1 conditions, when said first symmetric key is distributed, or previously distributed symmetric key are satisfied when use of period expires, number control method of fixed authentication method. In number of violations of the authentication method, when satisfied condition number 1, random number 1 from gateway receiving message including number 1; said number control method of fixed public key according to the random numbers and said number 1, number 2 message passing said gateway server signature said random number 1; said gateway in the event of a successful verification of the electronic signature by using message said said number 2, symmetrical key receiving said gateway; and said encrypted symmetric key decrypts and said obtaining including symmetrical, number violations of the authentication method. According to Claim 7, said symmetric key acquisition success message sending to the gateway indicating said number 3; and said symmetric key use the bus number 4 indicative message further including receiving from said gateway, number violations of the authentication method. According to Claim 7, receiving a message from said number violations of the random number 2 including number 5; said message authentication code (MAC) using a random number of said number 2 symmetrical generating; and said random number of said gateway a message authentication code generated number 2 number 6 message further including, number violations of the authentication method. According to Claim 9, said gateway, a message authentication code received from said number of violations of the random number 2, said symmetric key and said number 2 itself by using a random compared to generate message authentication code authenticating said number anxiety, number control method of fixed authentication method. According to Claim 9, said number 5 the transmission of message receipt and said number 6, valid performed periodically during said symmetric key, number control method of fixed authentication method. According to Claim 7, said number 1 conditions, when said first symmetric key is distributed, or previously distributed symmetric key are satisfied when use of period expires, number control method of fixed authentication method. Number 1 to number 12 either program for executing method according to number control method of fixed authentication anti anti anti computer decipherable recording medium. In number of violations of the authentication method, obtaining Certificate number 1 from said number control method of fixed during production number 1 device; said number 1 device including the steps of transmitting said number 1 key Certificate said number control method of fixed disclosure; random number 1 from receiving said number 1 device; and said number 1 device random number encrypted by said number 1 device enters said number 1 disclosure key is said number control method of fixed step of transmitting to a including, number violations of the authentication method. According to Claim 14, which when mounted on said number control method of fixed vehicle after the number 2 device, transferring said number 1 Certificate said number 2 device; said number 2 device from obtaining Certificate number 2 of said number 2 device; and determining said number 2 provided to corresponding to the selected gateway Certificate number 2 device including, number violations of the authentication method. According to Claim 15, random number 2 from receiving said number 2 device; said number to said number 2 device by encrypting key to decrypt said number 2 device is disclosure control method of fixed steps of transmitting said number 2 including a random number, number violations of the authentication method. According to Claim 15, violations of the production equipment and the diagnosis apparatus or said number 1 device number, said number 2 device including the gateway, number violations of the authentication method. According to Claim 16, is said number 2 device, said number anxiety and added to the list number 1, number 3 device number 1 from list if requested, said number 3 device list to the number [...] said number 1, number violations of the authentication method. According to Claim 18, is said number 3 device, said number 1 to number 4 device may then update the list to said number 1 to number the [...] said number 4 device list is list number 2, number violations of the authentication method. According to Claim 19, said number 3 device is, said number 2 list update result received from said number 4 device and, when said number 2 device notifies the error list said number 1, number violations of the authentication method. According to Claim 19, said number 2 device and includes a gateway, said number 3 device is diagnostic that comprises a, the printing system can comprise said number 4 device, said number 1 list local list which, global a playlist including at least one local list information list said number 2, number violations of the authentication method. According to Claim 18, said number 1 list, vehicle information, authentication number control method of fixed number, number violations of the individual identification information, a list including at least one of the electronic signature of said number 2 device said number 1, number violations of the authentication method.