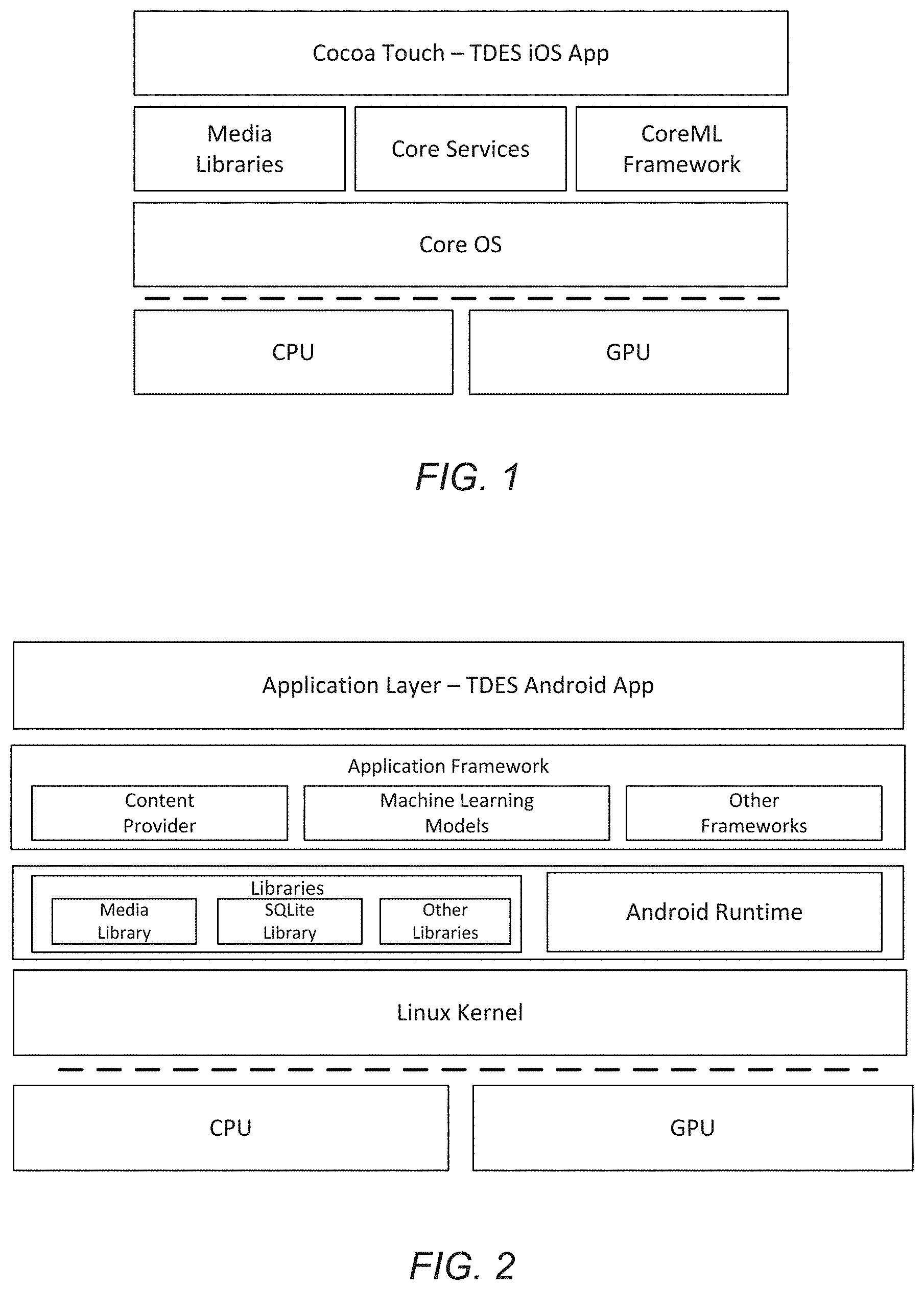
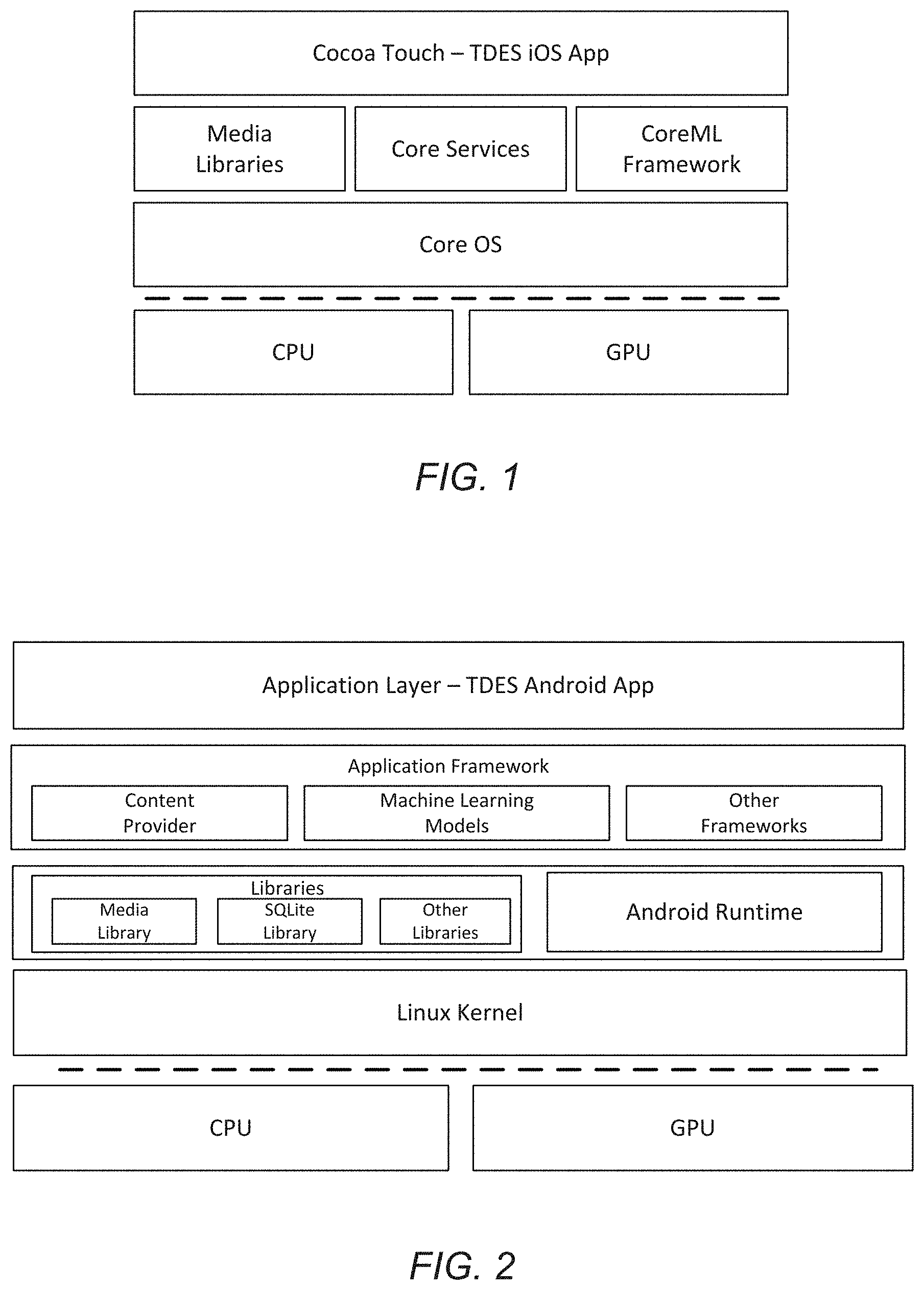
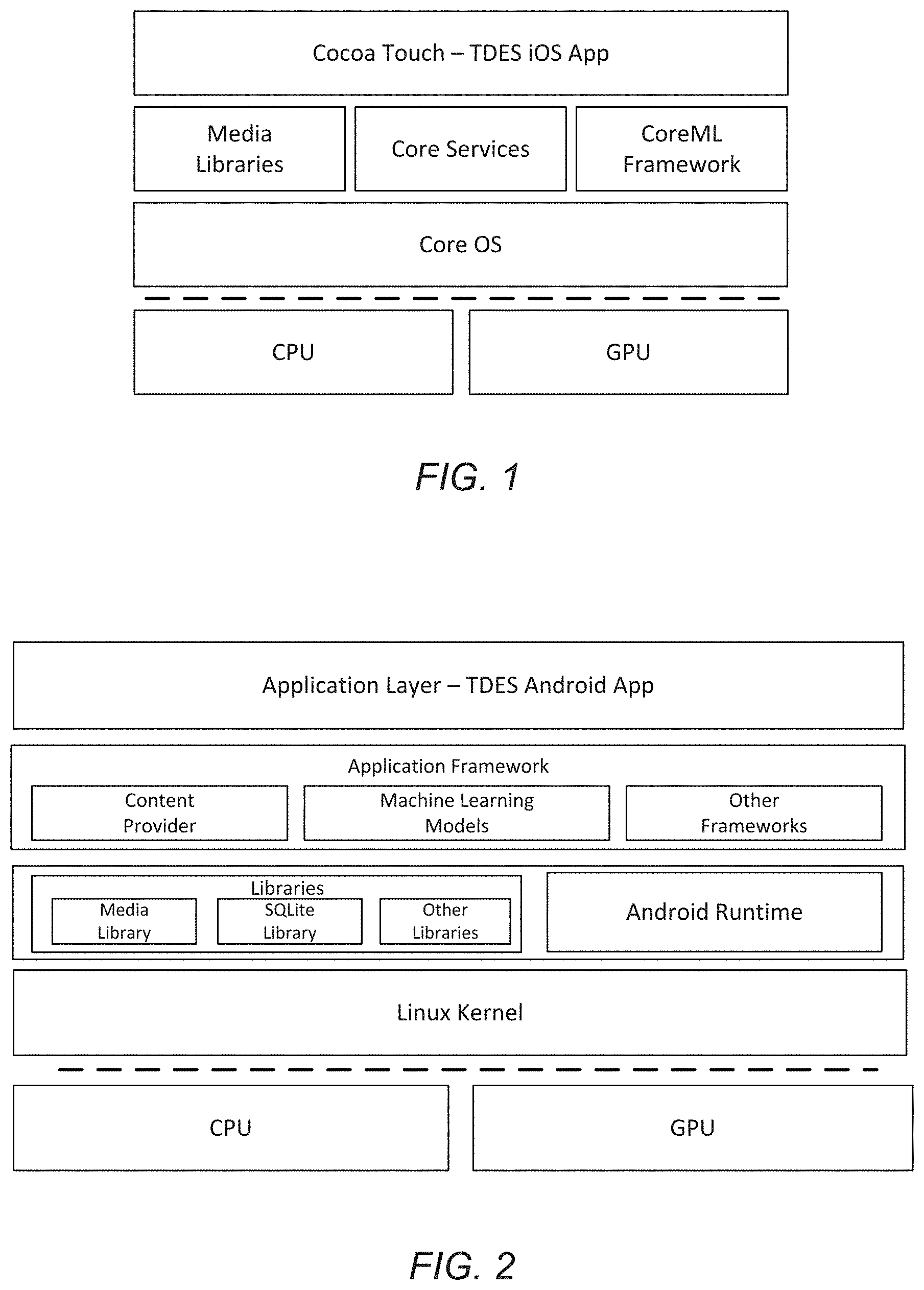
Targeted data extraction system and method
29-11-2022 дата публикации
Номер:
US0011513812B2
Автор: SUDHIR AGGARWAL, Gokila Dorai, Umit Karabiyik, Tathagata Mukherjee, Nicholas A Guerra, Manuel Hernandez-Romero, James Parsons, Khushboo Rathi
Контакты:
Номер заявки: 92-50-1673
Дата заявки: 06-01-2020



CPC - классификация
GG0G06G06FG06F1G06F16G06F16/G06F16/9G06F16/90G06F16/903G06F16/9035G06F9G06F9/G06F9/4G06F9/44G06F9/440G06F9/4406G06F9/441G06F9/4416HH0H04H04LH04L2H04L22H04L220H04L2209H04L2209/H04L2209/8H04L2209/80H04L9H04L9/H04L9/0H04L9/06H04L9/064H04L9/0643H04L9/3H04L9/32H04L9/326H04L9/3263H04WH04W4H04W4/H04W4/8H04W4/80IPC - классификация
GG0G06G06FG06F1G06F15G06F15/G06F15/1G06F15/17G06F15/177G06F16G06F16/G06F16/9G06F16/90G06F16/903G06F16/9035G06F9G06F9/G06F9/0G06F9/00G06F9/4G06F9/44G06F9/440G06F9/4401HH0H04H04LH04L9H04L9/H04L9/0H04L9/06H04MH04M1H04M1/H04M1/7H04M1/72H04M1/725H04M1/7251H04M1/72513H04WH04W1H04W12H04W12/H04W12/4H04W12/47H04W12/5H04W12/50H04W4H04W4/H04W4/8H04W4/80Цитирование НПИ
348/E7.083379/93.08
455/41.2
455/418
709/206
709/224
Abadi, et al., “Tensorflow: a system for large-scale machine learning.” in OSDI, vol. 16, 2016, pp. 265-283.
Aminnezhad, et al., “A survey on privacy issues in digital forensics,” IJCSDF, vol. 1, No. 4, pp. 311-323, 2012. Aminnezhad.
Anglano, “Forensic analysis of whatsapp messenger on android smartphones,” Digital Investigation, vol. 11, No. 3, pp. 201-213, 2014.
Bergstra, et al., “Theano: Deep learning on gpus with python,” in NIPS 2011, BigLearning Workshop, Granada, Spain, vol. 3. Citeseer, 2011.
Cantrell, et al., “Research toward a partiallyautomated, and crime specific digital triage process model,” Computer and Information Science, vol. 5, No. 2, p. 29, 2012.
Cho, et al., “Learning phrase representations using mn encoder-decoder for statistical machine translation,” arXiv preprint arXiv:1406.1078, 2014.
Howard, et al., “Mobilenets: Efficient convolutional neural networks for mobile vision applications,” arXiv preprint arXiv:1704.04861, 2017.
Husain, et al. “A simple cost-effective framework for iphone forensic analysis,” in Digital Forensics and Cyber Crime. Springer, 2010, pp. 27-37.
Jia, et al., “Caffe: Convolutional architecture for fast feature embedding,” in Proceedings of the 22nd ACM international conference on Multimedia. ACM, 2014, pp. 675-678.
Khan, et al., “Network forensics: Review, taxonomy, and open challenges,” Journal of Network and Computer Applications, 2016.
Krizhevsky, et al., “Imagenet classification with deep convolutional neural networks,” in Advances in neural Information processing systems, 2012.
Lawton, et al., “E-discovery in digital forensic investigations,” Technical Report CAST publication, Tech. Rep., 2014.
Lecun, et al., “Deep learning,” nature, vol. 521, No. 7553, 2015.
Murphy, Machine learning: a probabilistic perspective. MIT press, 2012.
Mutawa, et al., “Forensic analysis of social networking applications on mobile devices,” Digital Investigation, vol. 9, pp. S24-S33, 2012.
Quick, et al., “Forensic analysis of the android file system yaffs2,” 2011.
Roussev, “Forensic acquisition of cloud drives,” arXiv preprint arXiv:1603.06542, 2016.
Roussev, “Real-time digital forensics and triage,” Digital Investigation, vol. 10, No. 2, pp. 158-167, 2013.
Scrivens, et al., “Android digital forensics: data, extraction and analysis,” in Proceedings of the ACM Turing 50th Celebration Conference—China. ACM, 2017, p. 26.
Stirparo, et al., “The mobileak project: Forensics methodology for mobile application privacy assessment,” in Internet Technology and Secured Transactions, 2012 International Conference for. IEEE, 2012, pp. 297-303.
Szegedy, et al., “Rethinking the inception architecture for computer vision,” in Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, 2016, pp. 2818-2826.