SECURE DEPLOYMENT OF PROVABLE IDENTITY FOR DYNAMIC APPLICATION ENVIRONMENTS
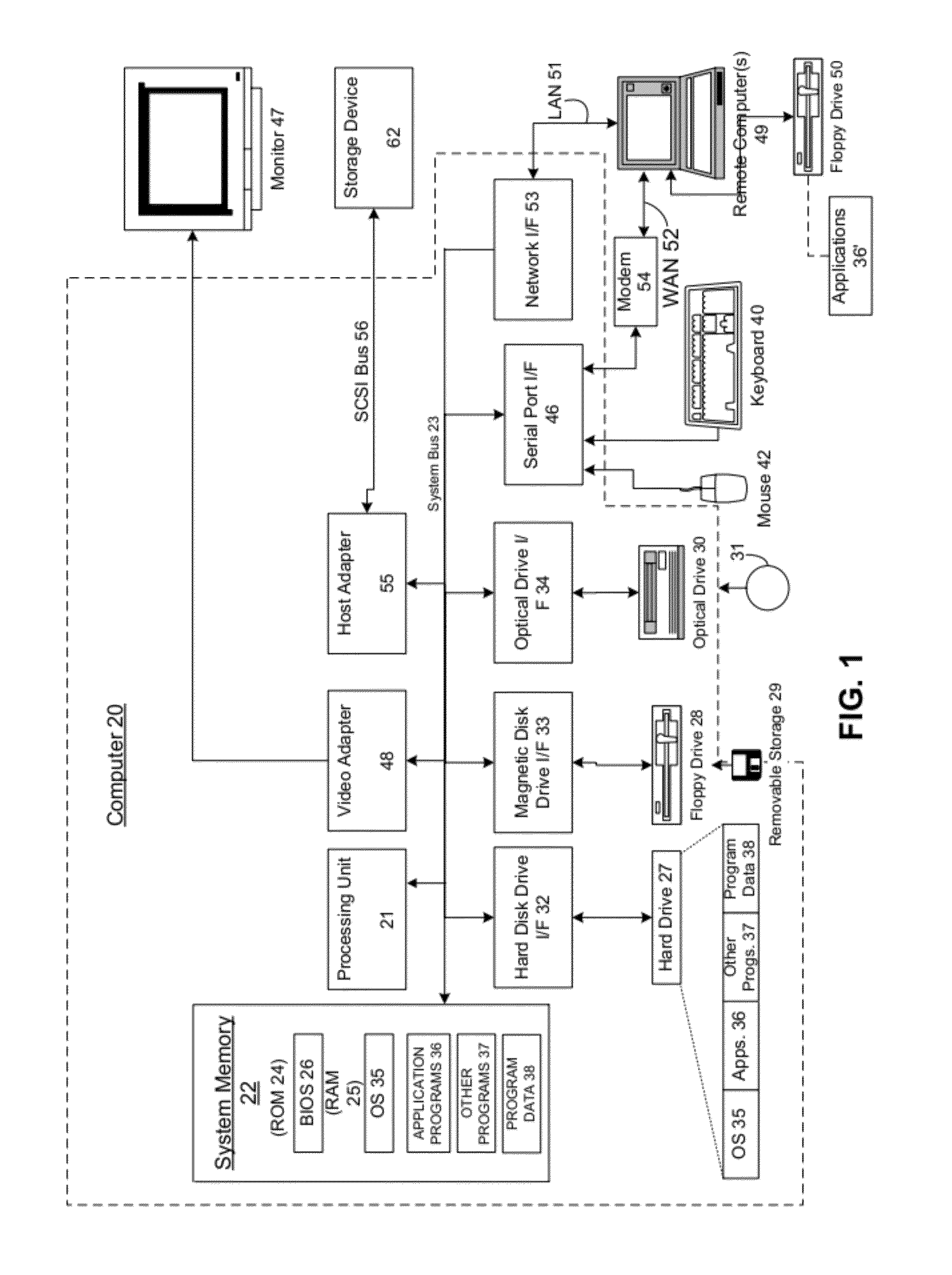
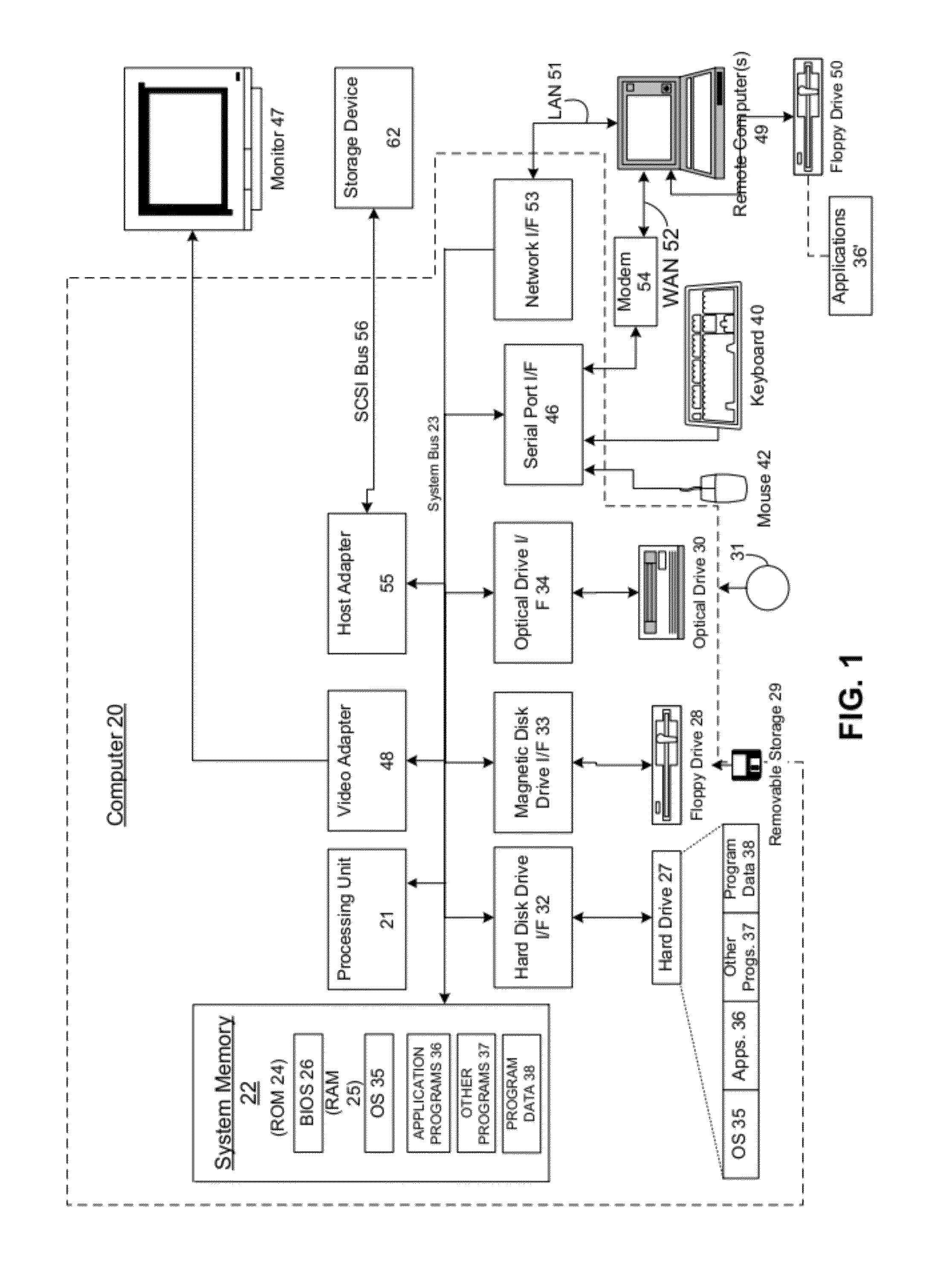
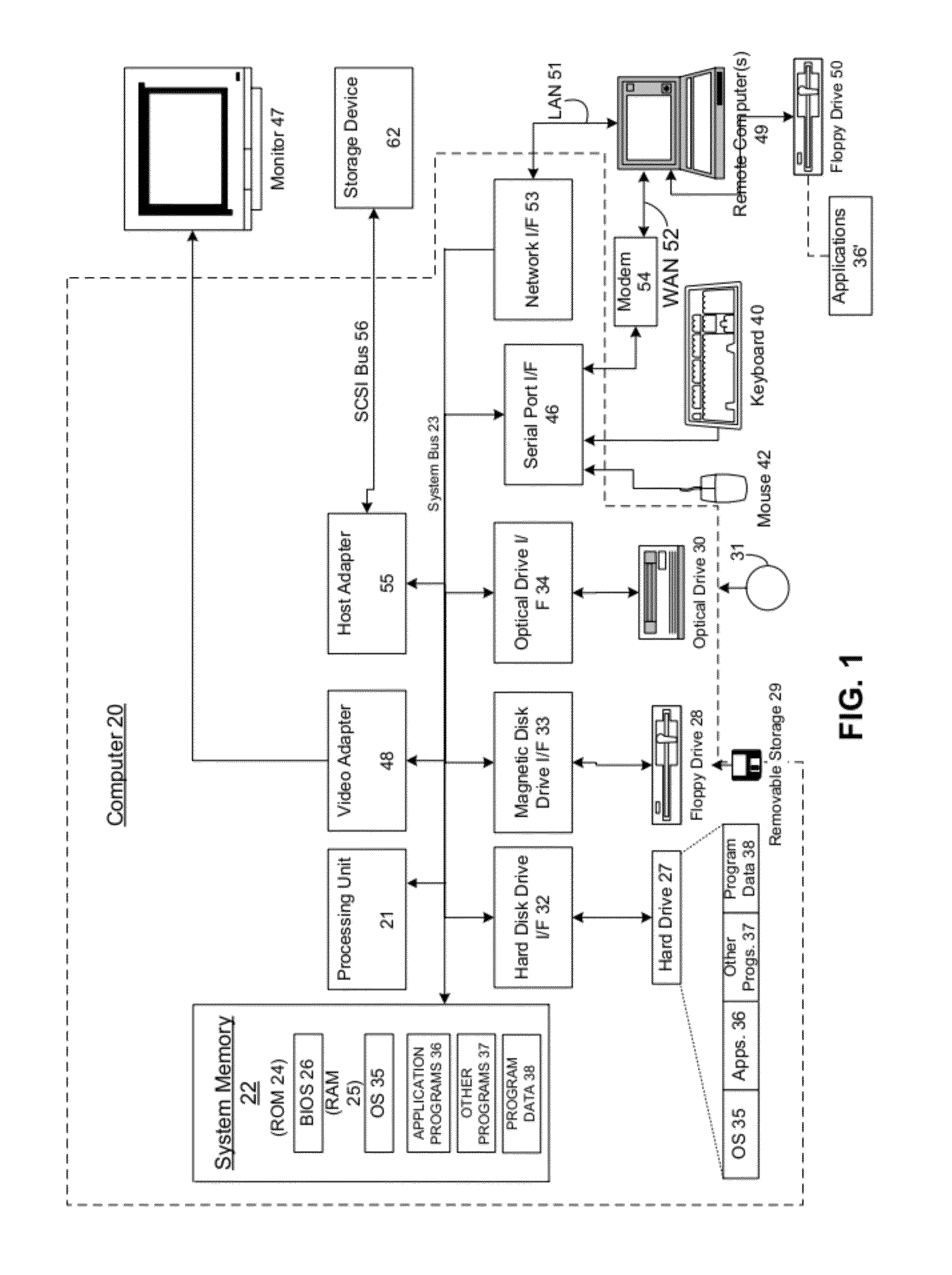
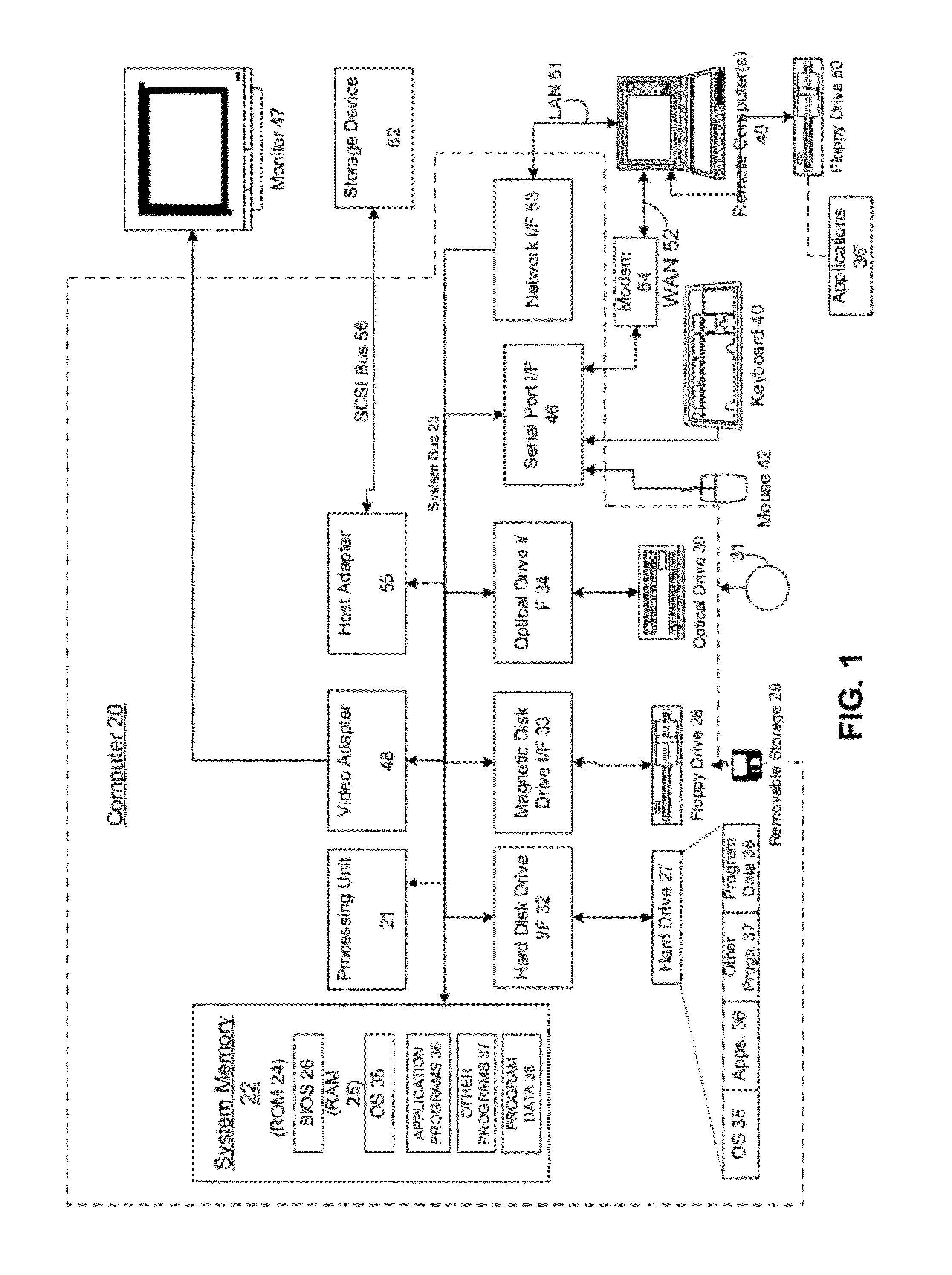
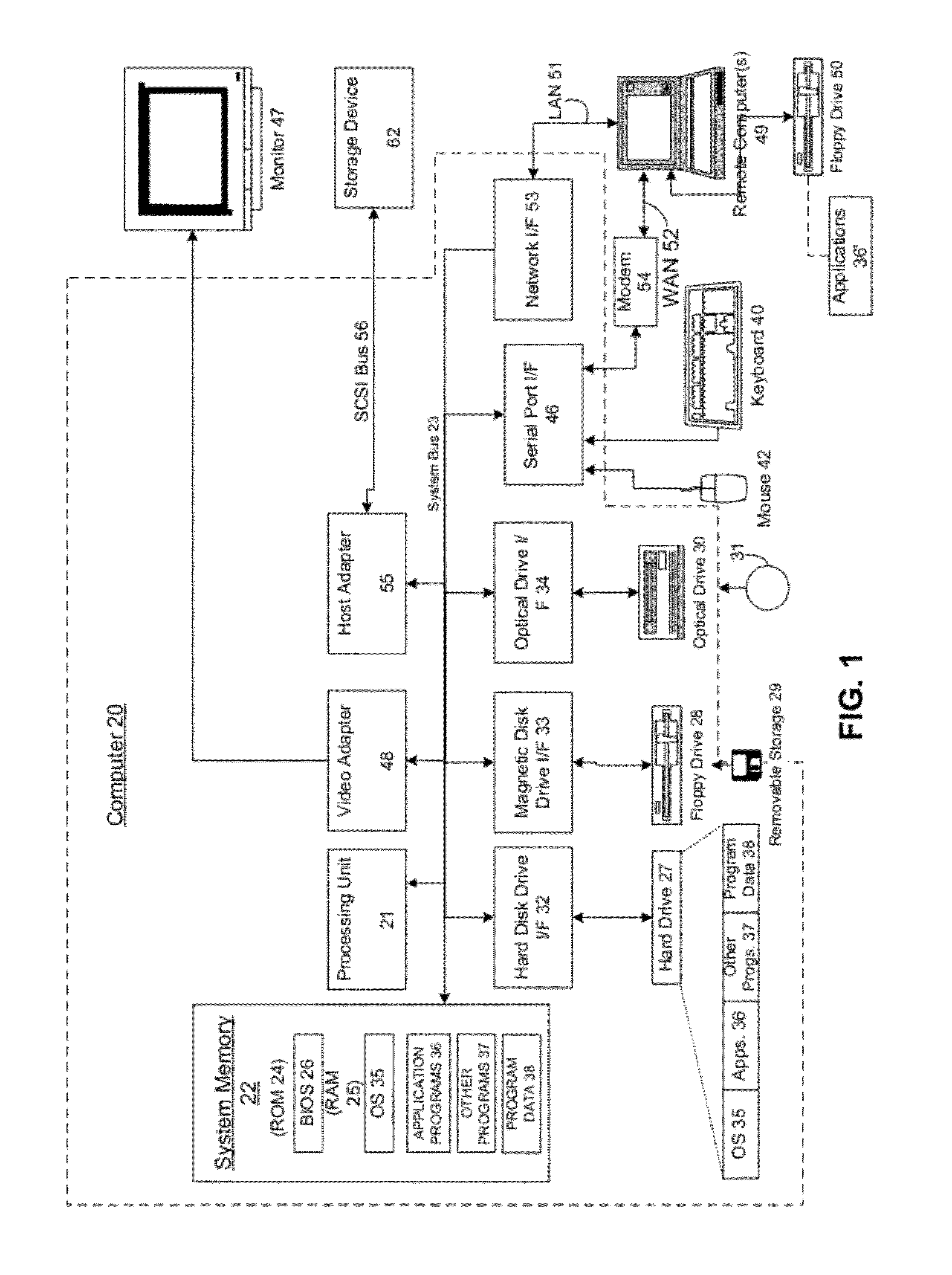
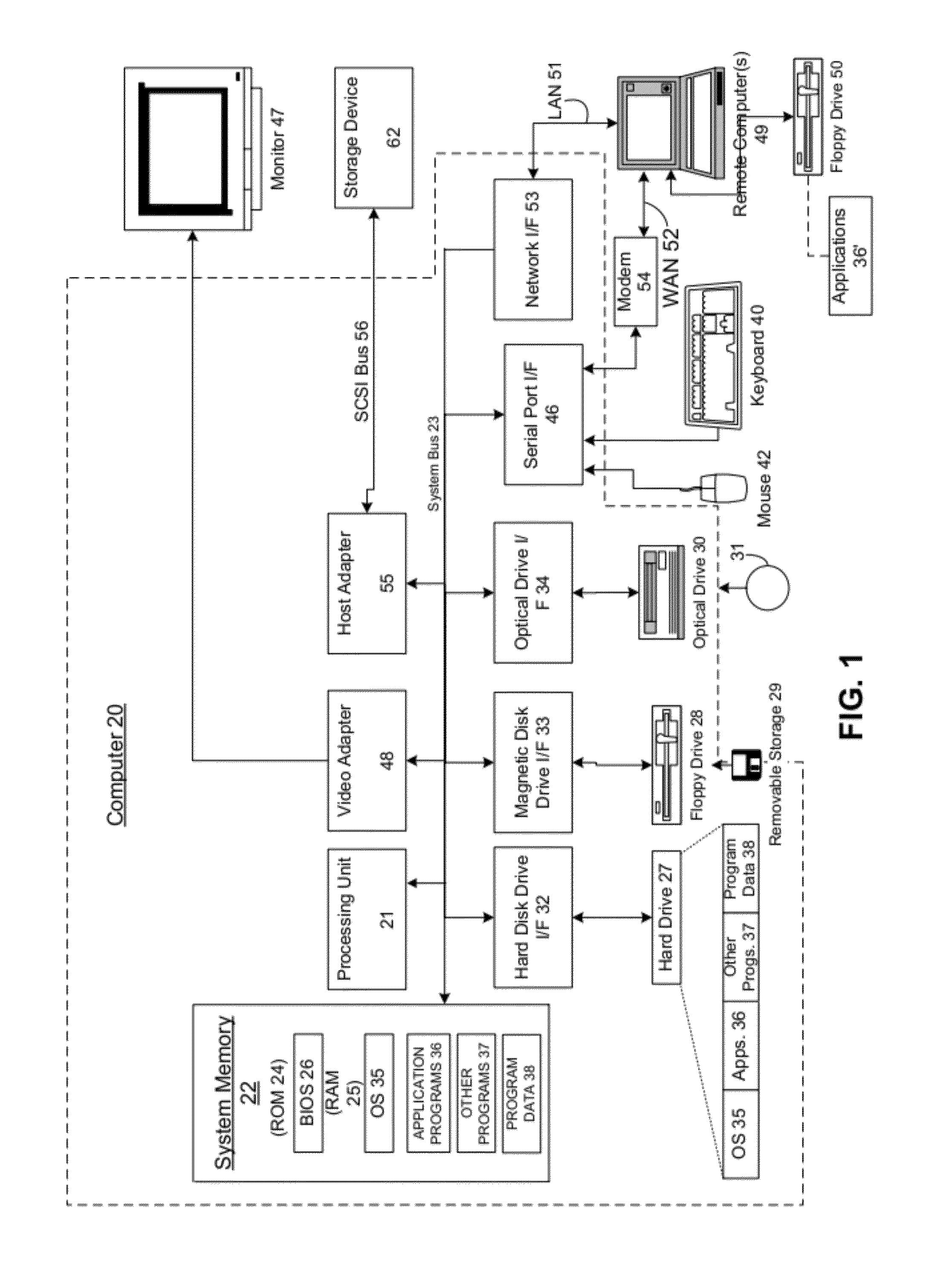
It is common for computers to communicate securely. A computer may have a provable identity that another computer can evaluate to determine that the first computer is the computer that it purports to be (e.g. a particular company's login and authorization server). It is also common for companies or other entities to deploy server farms made up of virtual machines (VMs). In such server farms, multiple VMs may be configured homogenously and serve resources to clients—such as remote desktops or remote applications. In the course of managing such a server farm, VMs may be destroyed and (re)created. A VM may be destroyed and then recreated for a variety of reasons, such as to prevent drift from a known machine state by recreating it with a known machine state. In these deployments where VMs are destroyed and created, each VM may have a provable identity. There are many problems with establishing a provable identity for a VM of a deployment, some of which are well known. It would therefore be an improvement over the prior art to provide techniques for establishing a provable identity for a VM of a server farm. One problem that prior techniques have, and which is reduced or eliminated by the present invention is that of the amount of time they require to establish a VM's provable identity. The prior techniques require a relatively large amount of time to carry out. This time cost may not be a major issue in a static environment, where once a machine is set up, it will run for an extended period of time. However in a VM deployment environment, such as a MICROSOFT Azure cloud computing platform, VMs may have a relatively short life, and may be recreated many times. This large number of creation events and the relatively short life of a VM after creation means that this relatively large cost in establishing a provable identity for the VM upon creation will occupy a large amount of the VM's time, and the VM will have less time when it is fully functional. In an embodiment of the present invention, a controller manages the VMs of a server farm. This controller may be, for example, MICROSOFT's Azure Fabric Controller, which monitors, maintains and provisions VMs in a MICROSOFT Azure cloud computing environment deployment. The deployment also comprises a security token service that is configured to provide clients of the server farm with tokens that the clients can use to confirm the provable identity of a VM in the server farm. In an embodiment, when the controller deploys a new VM instance, it injects a piece of cryptographic data (a “secret”) into the image file that the VM will boot from. Other embodiments may implement other ways of communicating a secret, such as via a separately established security network channel, or where the VM generates the secret and transmits it to the controller over a secure network channel. The controller sends this same cryptographic data (or other cryptographic data corresponding to the cryptographic data, such as where the cryptographic data is a private key, and the other cryptographic data is a public key of an asymmetrical key pair) to the security token service, along with other information that the security token service uses to generate a claim for The new VM. After the controller deploys the new VM instance, the new VM sends the security token service proof that it possesses the secret via a security protocol, and in response receives a full claim token. When a client connects to the server farm, it will attempt to establish the provable identity of the VM to which it connects. To do so, the client retrieves a public key from the security token service that the security token service uses to sign claims. The client also receives the full claim token from the VM, and uses the public key from the security token service and the full claim token from the VM to determine whether or not the VM's identity is proven. The example embodiments described herein discuss a situation where a client connects to a VM of a server farm. As described, the client may be thought of as performing a role traditionally considered to be performed by a server—that of authenticating the VM's identity. There are also embodiments where the roles are reversed in a communication, where the VM authenticates the client's identity. In either type of embodiment, the invention for establishing a secure provable identity of a VM of a server farm may be deployed. In another embodiment, the invention is implemented when the controller redeploys a single application instance into another VM host within the server farm (or even in a different data center, if the application migrates, for instance, due to geographic constraints). Application instances might move around frequently due to the underlying operating system undergoing security patching, or rebooting, or where the underlying hardware experiences a failure. Thus, the invention provides a secure provable identity that is durable across space and time, so even if the application instance is forcibly moved to a different physical server, the secure provable identity remains constant. This is an improvement over prior techniques, where a secure provable identity was bound to the underlying physical hardware. The systems, methods, and computer-readable media for establishing a provable identity for a virtual machine of a server farm are further described with reference to the accompanying drawings in which: Embodiments may execute on one or more computer systems. The term processor used throughout the description can include hardware components such as hardware interrupt controllers, network adaptors, graphics processors, hardware based video/audio codecs, and the firmware used to operate such hardware. The term processor can also include microprocessors, application specific integrated circuits, and/or one or more logical processors, e.g., one or more cores of a multi-core general processing unit configured by instructions read from firmware and/or software. Logical processor(s) can be configured by instructions embodying logic operable to perform function(s) that are loaded from memory, e.g., RAM, ROM, firmware, and/or mass storage. Referring now to A number of program modules comprising computer-readable instructions may be stored on computer-readable media such as the hard disk, magnetic disk 29, optical disk 31, ROM 24 or RAM 25, including an operating system 35, one or more application programs 36, other program modules 37 and program data 38. Upon execution by the processing unit, the computer-readable instructions cause the actions described in more detail below to be carried out or cause the various program modules to be instantiated. A user may enter commands and information into the computer 20 through input devices such as a keyboard 40 and pointing device 42. Other input devices (not shown) may include a microphone, joystick, game pad, satellite dish, scanner or the like. These and other input devices are often connected to the processing unit 21 through a serial port interface 46 that is coupled to the system bus, but may be connected by other interfaces, such as a parallel port, game port or universal serial bus (USB). A monitor 47, display or other type of display device can also be connected to the system bus 23 via an interface, such as a video adapter 48. In addition to the display 47, computers typically include other peripheral output devices (not shown), such as speakers and printers. The exemplary system of The computer 20 may operate in a networked environment using logical connections to one or more remote computers, such as a remote computer 49. The remote computer 49 may be another computer, a server, a router, a network PC, a peer device or other common network node, and typically can include many or all of the elements described above relative to the computer 20, although only a memory storage device 50 has been illustrated in When used in a LAN networking environment, the computer 20 can be connected to the LAN 51 through a network interface or adapter 53. When used in a WAN networking environment, the computer 20 can typically include a modem 54 or other means for establishing communications over the wide area network 52, such as the Internet. The modem 54, which may be internal or external, can be connected to the system bus 23 via the serial port interface 46. In a networked environment, program modules depicted relative to the computer 20, or portions thereof, may be stored in the remote memory storage device. It will be appreciated that the network connections shown are exemplary and other means of establishing a communications link between the computers may be used. Moreover, while it is envisioned that numerous embodiments of the present disclosure are particularly well-suited for computerized systems, nothing in this document is intended to limit the disclosure to such embodiments. System memory 22 of computer 20 may comprise instructions that, upon execution by computer 20, cause the computer 20 to implement the invention, such as the operational procedures of Generally, Continuing with the general description of As illustrated by In addition to receiving input from a client 201, draw commands can be received from applications and/or a desktop and be processed by the GDI 246. The GDI 246 in general can include a process that can generate graphical object draw commands. The GDI 246 in this example embodiment can be configured to pass its output to the remote presentation subsystem 254 where the commands are formatted for the display driver that is attached to the session. In certain example embodiments one or more physical displays can be attached to the server 204, e.g., in a remote presentation session situation. In these example embodiments the remote presentation subsystem 254 can be configured to mirror the draw commands that are rendered by the display driver(s) of the remote computer system and transmit the mirrored information to the client 201 via a stack instance associated with the session. In another example embodiment, where the server 204 is a remote presentation session server, the remote presentation subsystem 254 can be configured to include virtual display driver(s) that may not be associated with displays physically attacked to the server 204, e.g., the server 204 could be running headless. The remote presentation subsystem 254 in this embodiment can be configured to receive draw commands for one or more virtual displays and transmit them to the client 201 via a stack instance associated with the session. In an embodiment of the present invention, the remote presentation subsystem 254 can be configured to determine the display resolution for each display driver, e.g., determine the display resolution of the virtual display driver(s) associated with virtual displays or the display resolution of the display drivers associated with physical displays; and route the packets to the client 201 via the associated protocol stack instance. In some example embodiments the session manager 216 can additionally instantiate an instance of a logon process (sometimes referred to as a log in process) associated with the session identifier of the session that can be configured to handle logon and logoff for the session. In these example embodiments drawing commands indicative of the graphical user interface associated with the logon process can be transmitted to the client 201 where a user of the client 201 can input an account identifier, e.g., a username/password combination, a smart card identifier, and/or biometric information into a logon screen. The information can be transmitted to server 204 and routed to the engine 212 and the security subsystem 250 of the session core 244. For example, in certain example embodiments the engine 212 can be configured to determine whether the user account is associated with a license; and the security subsystem 250 can be configured to generate a security token for the session. Hypervisor microkernel 302 can enforce partitioning by restricting a guest operating system's view of system memory. Guest memory is a partition's view of memory that is controlled by a hypervisor. The guest physical address can be backed by system physical address (SPA), i.e., the memory of the physical computer system, managed by hypervisor. In an embodiment, the GPAs and SPAs can be arranged into memory blocks, i.e., one or more pages of memory. When a guest writes to a block using its page table, the data is actually stored in a block with a different system address according to the system wide page table used by hypervisor. In the depicted example, parent partition component 304, which can also be also thought of as similar to “domain 0” in some hypervisor implementations, can interact with hypervisor microkernel 302 to provide a virtualization layer. Parent partition 304 in this operational environment can be configured to provide resources to guest operating systems executing in the child partitions 1-N by using virtualization service providers 328 (VSPs) that are sometimes referred to as “back-end drivers.” Broadly, VSPs 328 can be used to multiplex the interfaces to the hardware resources by way of virtualization service clients (VSCs) (sometimes referred to as “front-end drivers”) and communicate with the virtualization service clients via communication protocols. As shown by the figures, virtualization service clients can execute within the context of guest operating systems. These drivers are different than the rest of the drivers in the guest in that they may be supplied with a hypervisor, not with a guest. Emulators 334 (e.g., virtualized integrated drive electronics device (IDE devices), virtualized video adaptors, virtualized NICs, etc.) can be configured to run within the parent partition 304 and are attached to resources available to guest operating systems 320 and 322. For example, when a guest OS touches a register of a virtual device or memory mapped to the virtual device 302, microkernel hypervisor can intercept the request and pass the values the guest attempted to write to an associated emulator. Each child partition can include one or more virtual processors (330 and 332) that guest operating systems (320 and 322) can manage and schedule threads to execute thereon. Generally, the virtual processors are executable instructions and associated state information that provide a representation of a physical processor with a specific architecture. For example, one virtual machine may have a virtual processor having characteristics of an INTEL x86 processor, whereas another virtual processor may have the characteristics of a PowerPC processor. The virtual processors in this example can be mapped to logical processors of the computer system such that the instructions that effectuate the virtual processors will be backed by logical processors. Thus, in an embodiment including multiple logical processors, virtual processors can be simultaneously executed by logical processors while, for example, other logical processors execute hypervisor instructions. The combination of virtual processors and memory in a partition can be considered a virtual machine. Guest operating systems can include any operating system such as, for example, a MICROSOFT WINDOWS operating system. The guest operating systems can include user/kernel modes of operation and can have kernels that can include schedulers, memory managers, etc. Generally speaking, kernel mode can include an execution mode in a logical processor that grants access to at least privileged processor instructions. Each guest operating system can have associated file systems that can have applications stored thereon such as terminal servers, e-commerce servers, email servers, etc., and the guest operating systems themselves. The guest operating systems can schedule threads to execute on the virtual processors and instances of such applications can be effectuated. The instances of VM 408 are hosted by a hosting layer 406 of a physical host 414. For instance, in a MICROSOFT Azure environment, hosting layer 406 may comprise an instance of Azure VM Host. Hosting layer 406 executes on a physical machine and is configured to enable multiple instances of VM 408 to run concurrently on the physical machine. Hosting layer 406 presents to a VM 408 a virtual operating platform and monitors the execution of VM 408 (and a guest operating system executing within VM 408). Security token service 404 is configured to create and manage accounts for VMs and other entities (such as fabric controller 402) within deployment 400. That is, security token service 404 is able to extend a chain of trust that it is part of to other entities within deployment 400. Security token service 404 itself may be considered trusted because client 412 is configured with information that allows it to validate security tokens issued by security token server 404. For example, client 412 may be configured with the certificate the security token service 404 uses to sign tokens that it passes to VMs 408. Alternatively, client 412 may be configured to possess the subject name of the certificate used by security token service 404 for signing tokens that it issues. A VM 408 may request a token from security token service 404. In that request, VM 408 proves its identity to security token service 404 by providing proof that it possesses the secret with which it was provisioned by fabric controller 402. Security token service 404 validates the identity of VM 408 using the account information (such as the VM's 408 public key) that was created by fabric controller 402. Security token service 404 then issues the token to the VM 408. The token is signed with the security token service's 404 private key. The VM 408 then sends the token to client 412, which validates that the token is signed by the security token service 404 using the information about the security token service's certificate with which client 412 is configured. Upon validation of the token, client 412 is able to check the identity asserted in the token for VM 408. An example communication flow for effectuating the present invention is also depicted in As a result of communication flow (1) and communication flow (5), client 412 now has both the public key of security token service 304 and the full token of VM-1408-1. It may then validate the full token (and, as a result, that VM-1408-1 does have the identity that it purports to have) with the public key. For instance, where a mathematical function that takes the public key and the full token as inputs produces a known output that matches what client 412 knows the output should match if VM-1408-1 does have the identity it purports to have, then client 412 may determine that VM-1408-1 does have the identity it purports to have. It may be appreciated that the present invention may be effectuated without adhering strictly to this communication flow of The primary difference between the embodiment of Like with respect to the communication flow of As depicted in Communication flow 2B depicts fabric controller 402 Communication flow 3B depicts fabric controller 402 The primary difference between the embodiment of Like with respect to the communication flow of As depicted in As depicted in After communication flows 1C, 2C, and 3C have occurred, client 412 In an embodiment where creating an account for the first computer on the second computer is performed by a fourth computer (such as fabric controller 402), and wherein the fourth computer has an account on the second computer and the authority to create accounts for other computers, operation 502 may include instructing the second computer, by the fourth computer, to create the account for the first computer. For instance, in Operation 504 depicts preparing the first computer to communicate on a communications network. Provisioning may comprise the fabric controller preparing the first computer/VM to operate, such as by creating the VM, and configuring it with the appropriate data and software to fulfill its function. Operation 506 depicts sending the first computer a full token that comprises an assertion of an identity of the first computer, the full token being created by the second computer, computer based on the account for the first computer. The token may comprise a claim of an identity of the first computer. In an embodiment, operation 506 is performed by the second computer (security token service 404). This may be similar to communication flow (4) of In an embodiment, operation 506 comprises sending to the first computer, by the second computer, the full token, in response to receiving a credential from the first computer corresponding to a credential stored in an account for the first computer on the second computer. For instance, when fabric controller 402 provisions VM-1408-1 and also creates an account for VM-1408-1 with security token service 404, it may send a credential (sometimes referred to as a secret) to both VM-1408-1 and security token service 404. Then, when VM-1408-1 wants to prove to security token service 404 that it is authorized to receive a full token for the account, it may present the credential to security token service 404 (such as by encoding it with security token service's 404 public key). Operation 508 depicts sending a public key to a third computer (such as client 412), wherein the third computer confirms the identity of the first computer based on determining that combining the full token of the first computer with the public key produces a result consistent with the identity of the first computer. This may comprise communication flows (1) and (5) of In an embodiment, operation 508 comprises the third computer determining to trust the full token because it was issued by the second computer, the third computer having validated an identity of the second computer. The third computer may have validated the identity of the second computer through determining that a domain name service name (such as a name provided through DNS) for the second computer matches a name in a certificate for the second computer (such as a Secure Sockets Layer—SSL—certificate). That client 412 trusts the full token at all may be based on a trusted-chain that extends from an entity that it trusts down to VM-1408-1. The top of this chain may be the Domain Name System (DNS)—that when client 412 queries DNS for the computer with name tokenservice.contoso.com and is directed to security token service 404, that that information is accurate. Client 412 may then authenticate a certificate presented by security token service 404 (that is issued by a certificate authority, or self-issued) as having the same name for the security token service as is obtained through DNS. Client 412 may then trust that security token service 412 has the identity it asserts to have. This chain of trust then extends to VM-1408-1 where VM-1408-1 is able to present to client 412 a full token that may be validated with the already-trusted security token service's 404 public key. Operation 510 depicts, in an embodiment where wherein creating an account for the first computer on the second computer is performed by a fourth computer, and further comprising: creating, by a fifth computer (such as a second instance of fabric controller 402), an account for a sixth computer (such as VM-2408-2), on the second computer; provisioning, by the fifth computer, the sixth computer; sending the sixth computer a second full token created by the second computer; and wherein sending the public key to the third computer comprises: sending the public key to the third computer, such that the third computer confirms an identity of the sixth computer based on processing the full token as presented by the second computer with the public key to produce a second known result. There may be cases where multiple fabric controllers 402 co-exist in a deployment, and each fabric controller is configured to communicate with security token service 404 to obtain full tokens on behalf of VMs 408 that they provision. In operation 510, a second fabric controller 402, provisions a second VM (such as VM-2408-2) and obtains from security token service 404 a second full token for this second VM 408. Operation 512 depicts sending the public key to a seventh computer (such as a second instance of client 412), such that the seventh computer confirms an identity of the first computer based on processing the full token as presented by the first computer with the public key to produce the known result. Multiple clients may validate the identity of a VM (such as VM-1408-1), using the same full token presented by the VM 408, as well as the same public key presented by security token service 404. Operation 514 depicts creating an account for an eighth computer (such as VM-N 408-N) on the second computer; provisioning the eighth computer; sending the eighth computer a second full token created by the second computer; and wherein sending the public key to the third computer comprises: sending the public key to the third computer, such that the third computer confirms an identity of the eighth computer based on processing the full token as presented by the eighth computer with the public key to produce a second known result. Where multiple VMs are provisioned with their own full token, each of these tokens may be validated by a client using the same public key of the security token service 404. As depicted in operation 514, a single client 412 uses one public key from security token service 404 to validate two full tokens—one for VM-1408-1 and one for VM-N 408-N. The operational procedures end with operation 516. It may be appreciated that there are embodiments of the invention that do not implement all of the operations of With respect to both Operation 604 depicts obtaining a full token from a computer, the full token indicating an identity of the computer. Operation 604 may occur in a manner similar to communication flow (5) of Operation 606 depicts validating the identity of the computer by processing the full token with the public key to produce a known result. Having obtained the public key of security token service 404 in operation 602, and the full token of VM-1408-1 in operation 604, client 412 now has both the public key and the full token, and may validate the full token (and thus, the identity of VM-1408-1) using the public key from security token service 404, which client 412 trusts. Operation 608 depicts communicating with the computer in a secure relationship. In operation 606, client 412 has validated the identity of VM-1408-1 to be that which VM-1408-1 asserts it is. Based on a chain of trust that extends down through security token service 404 and to VM-1408-1, client 412 may trust VM-1408-1, and as they communicate (such as where VM-1408-1 serves client 412 a remote presentation session), this communication may occur within a secure, or a trusted, relationship. The operational procedures of While the present invention has been described in connection with the preferred aspects, as illustrated in the various figures, it is understood that other similar aspects may be used or modifications and additions may be made to the described aspects for performing the same function of the present invention without deviating there from. Therefore, the present invention should not be limited to any single aspect, but rather construed in breadth and scope in accordance with the appended claims. For example, the various procedures described herein may be implemented with hardware or software, or a combination of both. Thus, the methods and apparatus of the disclosed embodiments, or certain aspects or portions thereof, may take the form of program code (i.e., instructions) embodied in tangible media, such as floppy diskettes, CD-ROMs, hard drives, or any other machine-readable storage medium. When the program code is loaded into and executed by a machine, such as a computer, the machine becomes an apparatus configured for practicing the disclosed embodiments. In addition to the specific implementations explicitly set forth herein, other aspects and implementations will be apparent to those skilled in the art from consideration of the specification disclosed herein. It is intended that the specification and illustrated implementations be considered as examples only. An invention is described for securely deploying a provable identity for virtual machines (VMs) in a dynamic environment. In an embodiment, a fabric controller instructs a VM host to create a VM and sends that VM a secret. The fabric controller sends that same secret (or a second secret, such as the private key of a public/private key pair) to the security token service along with an instruction to make an account for the VM. The VM presents proof that it possesses the secret to the security token service and in return receives a full token. When a client connects to the deployment, it receives the public key from the security token service, which it trusts, and the full token from the VM. It validates the full token with the public key to determine that the VM has the identity that it purports to have. 1. A method for establishing a provable identity for a first computer, comprising:
creating an account for the first computer on a second computer; configuring the first computer to communicate on a communications network; sending the first computer a full token that comprises an assertion of an identity of the first computer, the full token being created by the second computer based on the account for the first computer; and sending a public key to a third computer, wherein the third computer confirms the identity of the first computer based on determining that combining the full token of the first computer and the public key produces a result consistent with the identity of the first computer. 2. The method of instructing the second computer, by the fourth computer, to create the account for the first computer. 3. The method of 4. The method of the third computer determining to trust the full token because it was issued by the second computer, the third computer having validated an identity of the second computer through a domain name system. 5. The method of 6. The method of sending to the first computer, by the second computer, the full token, in response to receiving a credential from the first computer corresponding to a credential stored in an account for the first computer on the second computer. 7. The method of creating, by a fifth computer, an account for a sixth computer, on the second computer; configuring, by the fifth computer, the sixth computer to communicate on the communications network; sending the sixth computer a second full token that comprises an assertion of an identity of the sixth computer, the second full token being created by the second computer based on the account for the second computer; and wherein sending the public key to the third computer comprises:
sending the public key to the third computer, wherein the third computer confirms the identity of the sixth computer based on determining that combining the full token of the sixth computer and the public key produces a result consistent with the identity of the sixth computer. 8. The method of sending the public key to a seventh computer, such that the seventh computer confirms an identity of the first computer based on processing the full token as presented by the first computer with the public key to produce the known result. 9. The method of creating an account for an eighth computer on the second computer; configuring the eighth computer to communicate on the communications network; sending the eighth computer a second full that comprises an assertion of an identity of the eighth computer, the full token being token created by the second computer based on the account for the eighth computer; and wherein sending the public key to the third computer comprises:
sending the public key to the third computer, wherein the third computer confirms the identity of the eighth computer based on determining that combining the second full token of the eighth computer and the public key produces a result consistent with the identity of the eighth computer. 10. A system for establishing a provable identity for a first computer, comprising:
at least one processor; and at least one memory communicatively coupled to the at least one processor when the system is operational, the at least one memory bearing instructions that, upon execution by at least one processor, cause at least one processor to perform operations comprising:
creating an account for the first computer on a second computer; preparing the first computer to communicate on a communications network; sending the first computer a full token that comprises an assertion of an identity of the first computer, the full token being created by the second computer based on the account for the first computer; and sending a public key to a third computer, wherein the third computer confirms the identity of the first computer based on determining that combining the full token of the first computer and the public key produces a result consistent with the identity of the first computer. 11. The system of instructing the second computer, by the fourth computer, to create the account for the first computer. 12. The system of 13. The system of 14. The system of 15. The system of sending to the first computer, by the second computer, the full token, in response to receiving a credential from the first computer corresponding to a credential stored in an account for the first computer on the second computer. 16. The system of creating, by a fifth computer, an account for a sixth computer, on the second computer; preparing, by the fifth computer, the sixth computer to communicate on the communications network; sending the sixth computer a second full token that comprises an assertion of an identity of the sixth computer, the second full token being created by the second computer based on the account for the second computer; and wherein sending the public key to the third computer comprises:
sending the public key to the third computer, wherein the third computer confirms the identity of the sixth computer based on determining that combining the full token of the sixth computer and the public key produces a result consistent with the identity of the sixth computer. 17. The system of sending the public key to a seventh computer, wherein the seventh computer confirms the identity of the first computer based on determining that combining the full token of the first computer and the public key produces a result consistent with the identity of the first computer. 18. The system of creating an account for an eighth computer on the second computer; configuring the eighth computer to communicate on a communications network; sending the eighth computer a second full token that comprises an assertion of an identity of the first computer, the full token being created by the second computer based on the account for the eighth computer; and wherein sending the public key to the third computer comprises:
sending the public key to the third computer, wherein the third computer confirms the identity of the eighth computer based on determining that combining the full token of the first computer and the public key produces a result consistent with the identity of the first computer. 19. A computer-readable storage medium for establishing a provable identity for a virtual machine (VM), bearing computer-readable instructions that, upon execution by a computer, cause the computer to perform operations comprising:
creating an account on a token service for the VM; provisioning the VM; creating a secret for the VM; and sending the secret to the VM and to the token service, such that:
the VM sends proof of possession to the token service; in response to determining that the VM possesses the secret, the token service sends a full token to the VM; in response to receiving a request from an external computer for a public key of the token service, the token service sends the public key to the external computer; and the VM sends the full token to the external computer, such that the external computer validates an identity of the VM by processing the full token with the public key, and communicates with the VM. 20. The computer-readable storage medium of creating an account for a second VM on the token service; provisioning the second VM; creating a second secret for the second VM; and sending the secret to the second VM and to the token service, such that:
the second VM sends proof of possession of the second secret to the token service; in response to determining that the second VM possesses the second secret, the token service sends a second full token to the VM; and the second VM sends the second full token to the external computer, such that the external computer validates an identity of the second VM by processing the second full token with the public key, and communicates with the second VM.BACKGROUND
SUMMARY
BRIEF DESCRIPTION OF THE DRAWINGS
DETAILED DESCRIPTION OF ILLUSTRATIVE EMBODIMENTS