SYSTEM AND METHOD FOR REAL-TIME CUSTOMIZED THREAT PROTECTION
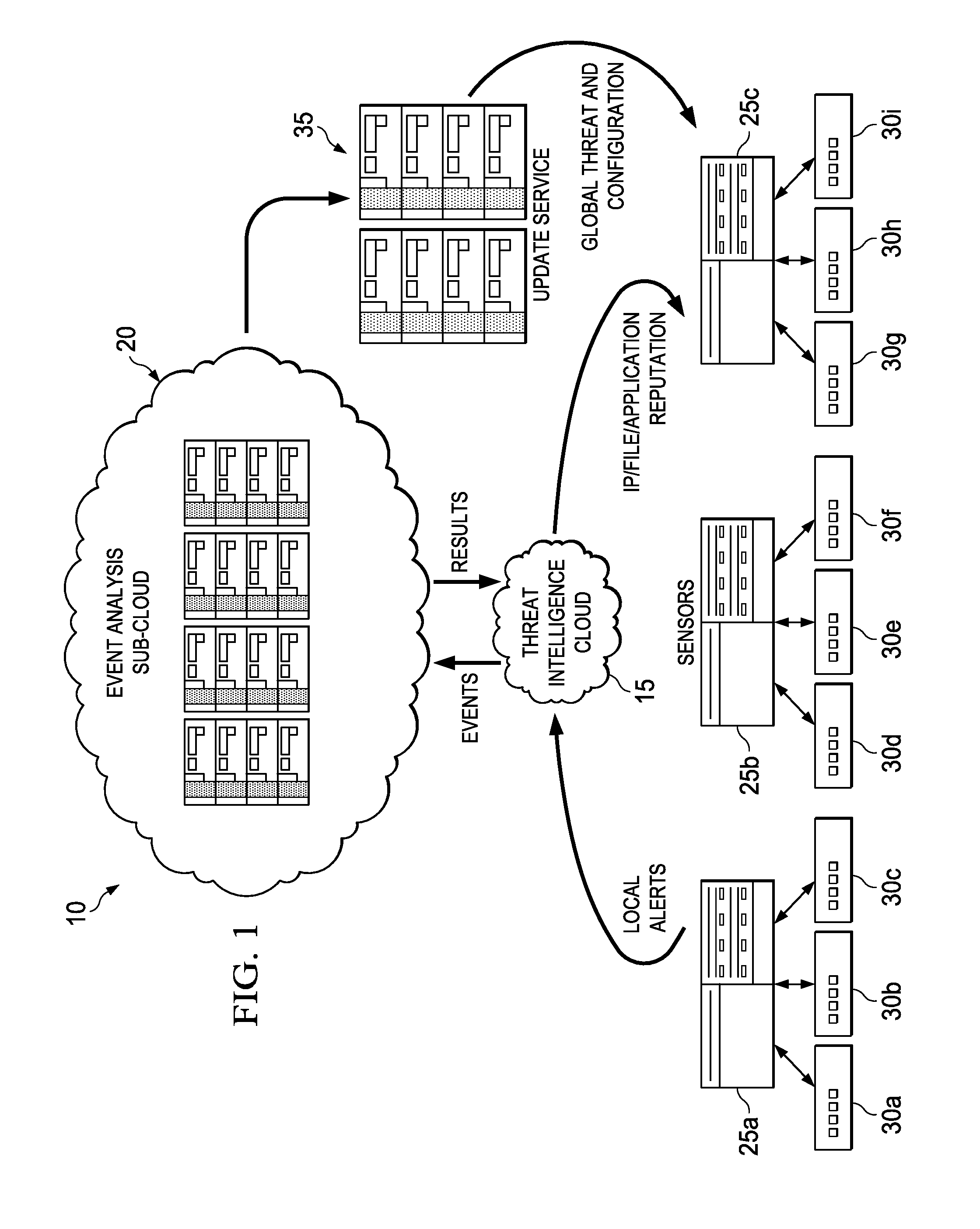
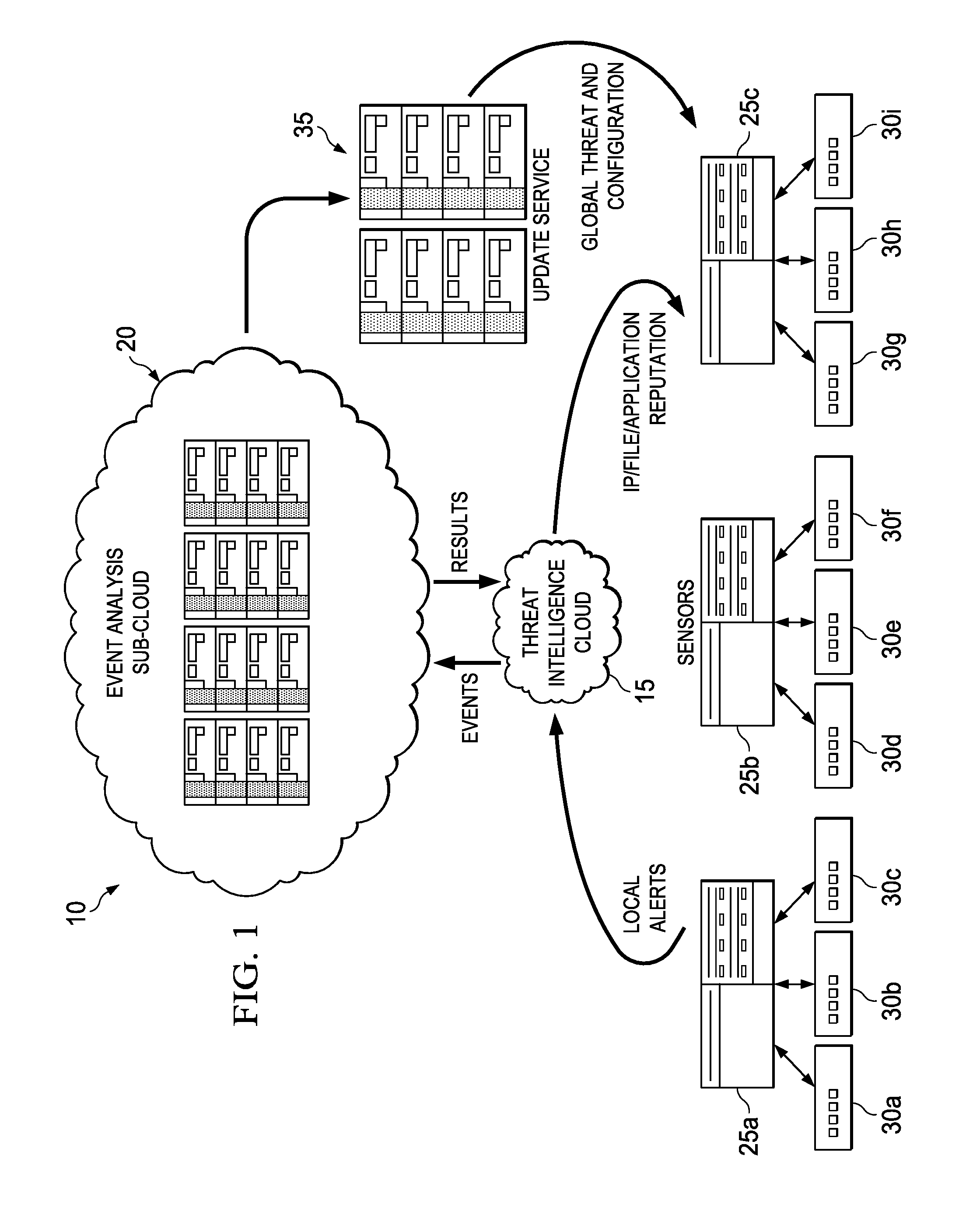
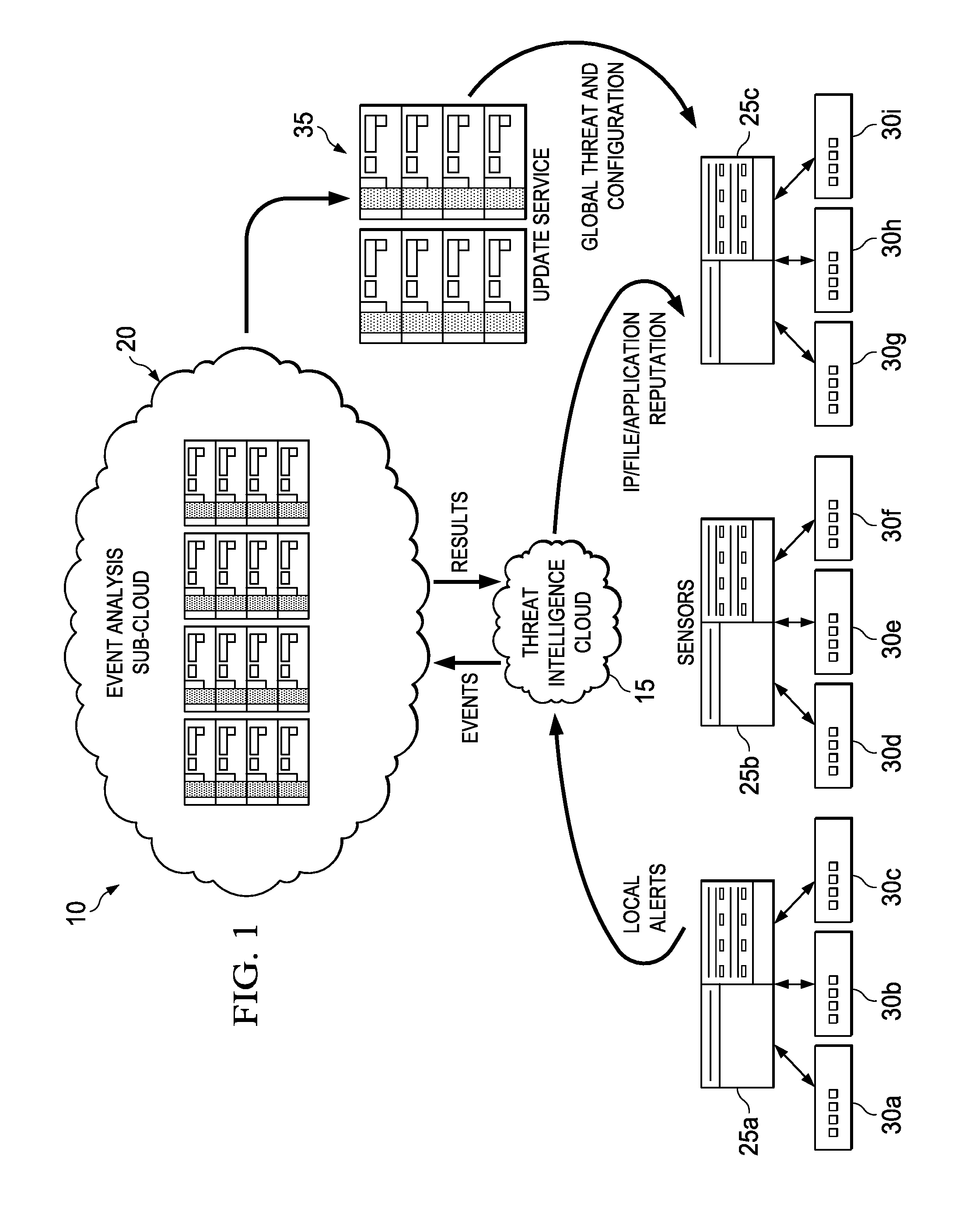
This specification relates in general to the field of network security, and more particularly, to a system and method for real-time customized threat protection. Information systems have become integrated into the daily lives of people and businesses on a global scale, and the field of information security has likewise become increasingly important in today's society. Such wide scaled integration has also presented many opportunities for malicious operators to exploit these systems. If malicious software can infect a host computer, it can perform any number of malicious actions, such as sending out spam or malicious emails from the host computer, stealing sensitive information from a business or individual associated with the host computer, propagating to other host computers, and/or assisting with distributed denial of service attacks. In addition, for some types of malware, a malicious operator can sell or otherwise give access to other malicious operators, thereby escalating the exploitation of the host computers. Thus, the ability to effectively protect and maintain stable computers and systems continues to present significant challenges for component manufacturers, system designers, and network operators. To provide a more complete understanding of the present disclosure and features and advantages thereof, reference is made to the following description, taken in conjunction with the accompanying figures, wherein like reference numerals represent like parts, in which: A method is provided in one example embodiment that includes receiving event information associated with reports from sensors distributed throughout a network environment and correlating the event information to identify a threat. A customized security policy based on the threat may be sent to the sensors. In more particular embodiments, the event information may be received from a threat intelligence cloud. In yet other embodiments, reputation data may also be sent to the threat intelligence cloud based on the threat. Turning to Each of the elements of Before detailing the operations and the infrastructure of A typical network environment includes the ability to communicate electronically with other networks, using the Internet, for example, to access web pages hosted on servers connected to the Internet, to send or receive electronic mail (i.e., email) messages, or to exchange files with end users or servers connected to the Internet. Users normally expect data stored in a network environment to be readily available but secure from unauthorized access. They also usually expect communications to be reliable and secure from unauthorized access. However, malicious users are continuously developing new tactics for interfering with normal operations and gaining access to confidential information. Viruses, Trojans, worms, bots, and other malware are common examples of vehicles used to exploit vulnerabilities in a network or system, but any activity designed to interfere with the normal operation of a computer or network through unauthorized access, destruction, disclosure, modification of data, and/or denial of service is a “threat.” A broad range of countermeasures can be deployed against threats, including firewalls, intrusion prevention systems, network access controls, and web filtering. An intrusion prevention system (IPS), also known as an intrusion detection and prevention system (IDPS), for example, can monitor network and/or system activities for malicious or potentially malicious activity and send an alert. IPS alerts, however, may not always be actionable. Many alerts provide only cautionary information or guidance, even if an observed event is indicative of malicious activity, since a single event may not be sufficient to identify an attack with a suitable degree of confidence. An IPS is typically placed in-line so that it can actively block detected intrusions, such as by dropping packets, resetting a connection, and/or blocking traffic from a source. An IPS can use multiple detection methods, including application and protocol anomaly, shell-code detection algorithms, and signatures. For example, signature-based detection generally includes comparing a signature (i.e., any pattern that corresponds to a known threat) against observed events or activity to identify a threat. An example signature is an attempt to establish a remote connection as a root user. Another example is receiving an email with a subject line and attached file that are characteristic of a known form of malware. Signature-based detection can be very effective at detecting a known threat, but can be ineffective at detecting an unknown threat, or even slight variations of a known threat. Moreover, IPS signatures tend to be universal and not generally customized for a local environment. Threats may only be seen locally, without a global view. Knowledge collected from sensors deployed globally cannot generally be leveraged to improve local security policy. Manual adjustment to policies is also often required, which may cause enough delay to allow an infection to spread. In accordance with embodiments described herein, network environment 10 can overcome these shortcomings (and others) by providing a system and method for correlating global threat intelligence and local threat intelligence, and providing a customized security policy. Referring again to Threat intelligence cloud 15 is a reputation system in one embodiment, which may be implemented as a distributed filesystem cluster. In general, a reputation system monitors activity and assigns a reputation value or score to an entity based on its past behavior. The reputation value may denote different levels of trustworthiness on the spectrum from benign to malicious. For example, a connection reputation value (e.g., minimal risk, unverified, high risk, etc.) may be computed for a network address based on connections made with the address or email originating from the address. Connection reputation systems may be used to reject email or network connections with IP addresses known or likely to be associated with malicious activity, while file reputation systems can block activity of files (e.g., applications) having hashes known or likely to be associated with malicious activity. Threat intelligence cloud 15 may receive reports from sensors (e.g., sensors 25 Event analysis sub-cloud 20 represents a cloud infrastructure for storing, processing, and mining events, both historically and in near real-time. Sub-cloud 20 may implement heuristics for data-mining alerts to correlate information from sensors distributed throughout a network (e.g., sensors 25 In certain embodiments, threat intelligence cloud 15 and event analysis sub-cloud 20 may both be implemented as cloud infrastructures. A cloud infrastructure in general is an environment for enabling on-demand network access to a shared pool of computing resources that can be rapidly provisioned (and released) with minimal service provider interaction. Thus, it can provide computation, software, data access, and storage services that do not require end-user knowledge of the physical location and configuration of the system that delivers the services. A cloud-computing infrastructure can include services delivered through shared data-centers, which may appear as a single point of access. Multiple cloud components, such as cloud 15 and sub-cloud 20, can communicate with each other over loose coupling mechanisms, such as a messaging queue. Thus, the processing (and the related data) need not be in a specified, known, or static location. Cloud 15 and sub-cloud 20 may encompass any managed, hosted service that can extend existing capabilities in real time. In regards to the internal structure associated with network environment 10, each of threat intelligence cloud 15, event analysis sub-cloud 20, sensors 25 Additionally, threat intelligence cloud 15, event analysis sub-cloud 20, sensors 25 Note that in certain example implementations, the functions outlined herein may be implemented by logic encoded in one or more tangible media (e.g., embedded logic provided in an ASIC, digital signal processor (DSP) instructions, software (potentially inclusive of object code and source code) to be executed by a processor, or other similar machine, etc.), which may be inclusive of non-transitory media. In some of these instances, memory elements can store data used for the operations described herein. This includes the memory elements being able to store software, logic, code, or processor instructions that are executed to carry out the activities described herein. In another example, the activities outlined herein may be implemented with fixed logic or programmable logic (e.g., software/computer instructions executed by a processor) and the elements identified herein could be some type of a programmable processor, programmable digital logic (e.g., a field programmable gate array (FPGA), an EPROM, an EEPROM) or an ASIC that includes digital logic, software, code, electronic instructions, or any suitable combination thereof. Any of the potential processing elements, modules, and machines described herein should be construed as being encompassed within the broad term “processor.” For example, a low-severity alert may be set for downloading a portable document format (PDF) file having JAVASCRIPT tags. A local policy may ignore such an event since it is a low-severity alert. However, the reputation and source of such a PDF may be determined based on reports received from multiple sensors throughout the network. By data mining events reported from the distributed sensors, the PDF document may be identified as a threat targeting a particular country, region, or industry by correlating events reported by sensors in that country, region, or industry. A host that downloaded this PDF file from a suspicious address with a bad reputation can also be identified. Suggestions, guidance, and policy change recommendations can then be provided. At 230, sub-cloud 20 may generate global threat information and inform all IPSs in network environment 10 or within a particular segment (e.g., associated with a particular country) of network environment 10, as well as provide customized security policy/configuration suggestions to them based on threat correlation. Customized security policies can include granular response actions to protect network environment 10 without intervention from an administrator. For example, update service 35 may provide a custom security policy to sensor 25 Thus, network environment 10 may provide significant advantages, some of which have already been described. More particularly, local security countermeasures can use locally tuned policy to provide protection against threats based on the local network's needs, and network environment 10 can connect each of the local sensors (i.e., sensors 25 Note that with the examples provided above, interaction may be described in terms of two, three, or four network elements. However, this has been done for purposes of clarity and example only. In certain cases, it may be easier to describe one or more of the functionalities of a given set of flows by only referencing a limited number of network elements. It should be appreciated that network environment 10 (and its teachings) are readily scalable and can accommodate a large number of components, as well as more complicated/sophisticated arrangements and configurations. It should also be appreciated that the principles described herein in the particular context of an IPS may be readily extended to other types of network elements, such as gateways, firewalls, etc., or to host systems, such as an antivirus system. Accordingly, the examples provided should not limit the scope or inhibit the broad teachings of network environment 10 as potentially applied to a myriad of other architectures. Additionally, although described with reference to particular scenarios, where operations may be associated with a given network element, these operations can be implemented externally, or consolidated and/or combined in any suitable fashion. In certain instances, certain elements may be provided in a single proprietary module, device, unit, etc. It is also important to note that the steps in the appended diagrams illustrate only some of the possible signaling scenarios and patterns that may be executed by, or within, network environment 10. Some of these steps may be deleted or removed where appropriate, or these steps may be modified or changed considerably without departing from the scope of teachings provided herein. In addition, a number of these operations have been described as being executed concurrently with, or in parallel to, one or more additional operations. However, the timing of these operations may be altered considerably. The preceding operational flows have been offered for purposes of example and discussion. Substantial flexibility is provided by network environment 10 in that any suitable arrangements, chronologies, configurations, and timing mechanisms may be provided without departing from the teachings provided herein. Numerous other changes, substitutions, variations, alterations, and modifications may be ascertained to one skilled in the art and it is intended that the present disclosure encompass all such changes, substitutions, variations, alterations, and modifications as falling within the scope of the appended claims. In order to assist the United States Patent and Trademark Office (USPTO) and, additionally, any readers of any patent issued on this application in interpreting the claims appended hereto, Applicant wishes to note that the Applicant: (a) does not intend any of the appended claims to invoke paragraph six (6) of 35 U.S.C. section 112 as it exists on the date of the filing hereof unless the words “means for” or “step for” are specifically used in the particular claims; and (b) does not intend, by any statement in the specification, to limit this disclosure in any way that is not otherwise reflected in the appended claims. A method is provided in one example embodiment that includes receiving event information associated with reports from sensors distributed throughout a network environment and correlating the event information to identify a threat. A customized security policy based on the threat may be sent to the sensors. 1. A method, comprising:
receiving event information associated with reports from sensors distributed throughout a network environment; correlating the event information to identify a threat; and sending a customized security policy to at least one of the sensors based on the threat. 2. The method of 3. The method of 4. The method of 5. The method of 6. The method of 7. The method of 8. Logic encoded in one or more non-transitory media that includes code for execution and when executed by one or more processors is operable to perform operations comprising:
receiving event information associated with reports from sensors distributed throughout a network environment; correlating the event information to identify a threat; and sending a customized security policy to at least one of the sensors based on the threat. 9. The encoded logic of 10. The encoded logic of 11. The encoded logic of 12. The encoded logic of 13. The encoded logic of 14. An apparatus, comprising:
one or more processors operable to execute instructions associated with an event analysis sub-cloud such that the apparatus is configured for:
receiving event information associated with reports from sensors distributed throughout a network environment; correlating the event information to identify a threat; and sending a customized security policy to at least one of the sensors based on the threat. 15. The apparatus of 16. The apparatus of 17. The apparatus of 18. The apparatus of 19. The apparatus of 20. An apparatus, comprising:
a threat intelligence cloud; an event analysis sub-cloud; and one or more processors operable to execute instructions associated with the threat intelligence cloud and the event analysis sub-cloud such that:
the threat intelligence cloud is configured for receiving event information associated with reports from sensors distributed throughout a network environment; and the event analysis sub-cloud is configured for correlating the event information to identify a threat and sending a customized security policy to at least one of the sensors based on the threat.TECHNICAL FIELD
BACKGROUND
BRIEF DESCRIPTION OF THE DRAWINGS
DETAILED DESCRIPTION OF EXAMPLE EMBODIMENTS
Overview
Example Embodiments