TECHNIQUES FOR TRUSTED LOCATION APPLICATION AND LOCATION PROVIDER COMMUNICATIONS
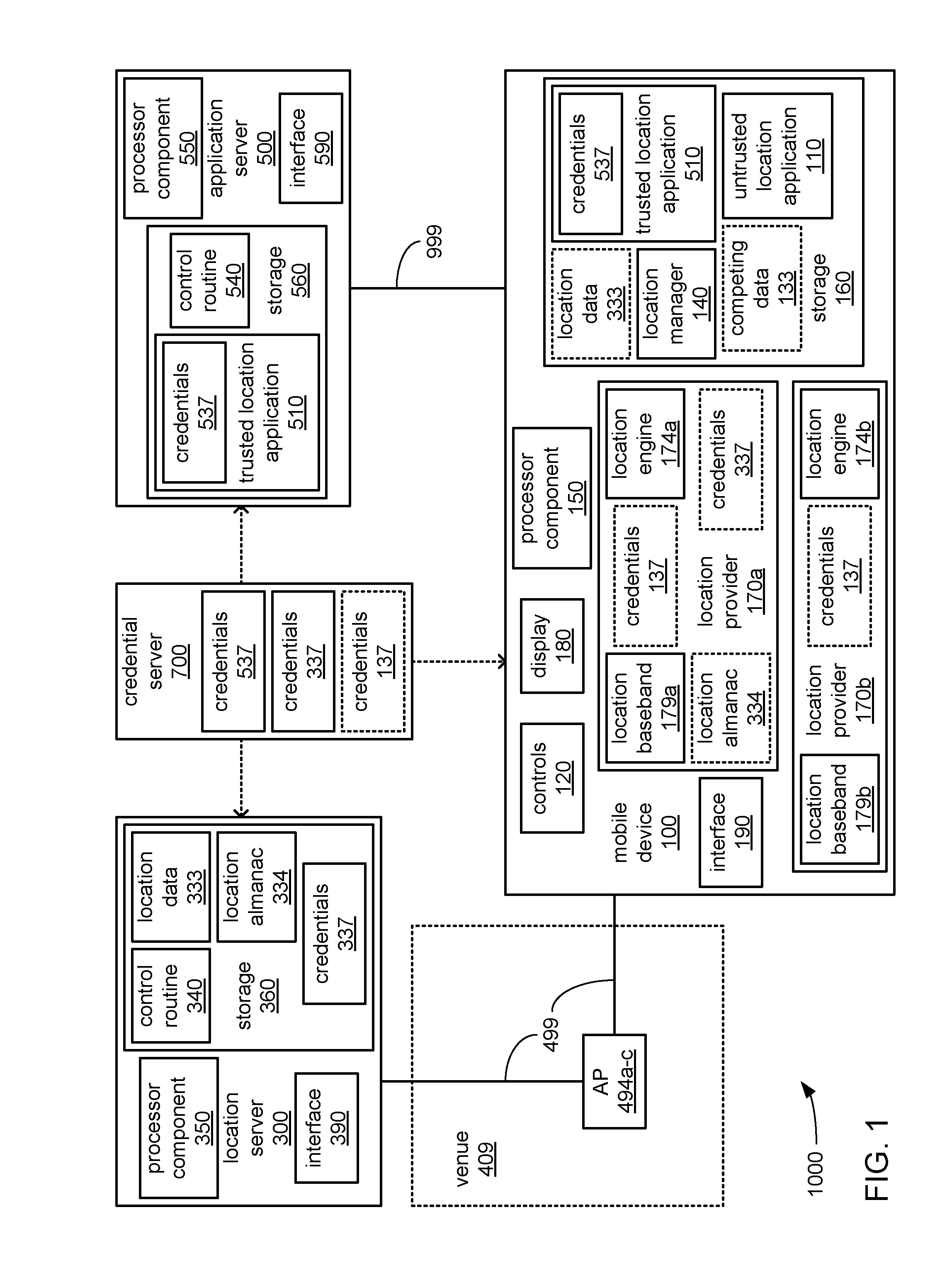
This application is continuation of, claims the benefit of and priority to previously filed U.S. patent application Ser. No. 14/128,615 filed Dec. 22, 2013, which is a national stage application of International Application No. PCT/US2013/062318, filed Sep. 27, 2013, which claims the benefit of and priority to previously filed U.S. Provisional Patent Application No. 61/813,761 filed Apr. 19, 2013; all of the above are hereby incorporated by reference in their entirety. Embodiments described herein generally relate to the establishment and use of trusted communications in exchanging location information among components of a mobile device to prevent unauthorized use of the location information. Mobile devices have long had the ability to track their own location relative to the surface of the Earth through receipt and analysis of wireless signals from multiple global positioning system (GPS) or global navigation satellite system (GNSS) satellites. Thus, users of such computing devices, whether carried on their persons or installed within vehicles, have long been able to view a visual presentation of where they are on the surface of the Earth at any given moment. Further, beyond simply presenting location information such as a current set of coordinates, mobile devices have long incorporated location applications to make use of such location information in providing other services (e.g., presenting weather predictions for a current location; presenting locations of shops or gas stations, along with their prices, etc., near a current position; etc.). More recently, mobile devices have been provided the ability to track their own location relative to an interior of a venue (e.g., an interior of a mall, a store, an airport terminal, etc.) with a finer location accuracy level than possible using signals emanating from satellites, which may also not be able to penetrate portions of such structures to reach their interiors. This is typically done by receiving and analyzing wireless signals emanating from wireless network access points (APs) forming a location network within such a venue, sometimes based on hyperbolic navigation principles. Further, such mobile devices have recently come to incorporate location applications to cooperate with location services provided by such a location network to guide users to locations of particular items of interest within a venue, such as products available for purchase, new products and/or products for which promotions are offered within that venue. Such location applications rely on a location provider of a mobile device that has been configured to interact with such location network providing such location services within a venue to determine a current location of the mobile device relative to rooms, hallways, aisles, shelves, kiosks, information desks, restrooms, etc. The location provider then provides the current location to a location application associated with the venue and able to correlate items of interest to the locations at which those items of interest are offered within that venue. Such correlations are then used to guide a user to items of interest and/or to present promotions (e.g., discounts) associated with those items. Unfortunately, typical system architectures within such mobile devices have been found to enable a form of “hijacking” of such location information by other location applications that may use such location information to present users with competing information intended to encourage users to leave that venue for a competing venue. More specifically, location information indicating a current location within one venue may be used by a location application of a competing venue to present a user with ads concerning competing products or services offered at the competing venue (sometimes referred to as a “showroom pushing threat”). In such architectures, location information from any location provider of a mobile device is typically freely distributed by a location manager of the mobile device to any location application requesting it from the location manager. The location manager is typically interposed between the location providers and the location applications to provide a platform-agnostic interface for the location applications. Though such free flowing provision of location information by the location manager was originally envisioned as being a benefit, in these situations, it has proven to enable malicious behavior by one location application against another. Further, the fact of the location manager typically being a component of an operating system (OS) of a mobile device has been known to render the location manager vulnerable to being corrupted to enable hijacking. Various embodiments are generally directed to techniques for conveying location information between a location provider and a trusted location application within a mobile device through trusted communications to preclude provision of the location information to an untrusted location application. The location provider may be one of multiple location providers incorporated into the mobile device, each employing a different technique to determine a current location of the mobile device (e.g., GPS, GNSS, motion sensing, triangulation from signal sources, WiFi-based RSSI or time-of-flight, etc.). The trusted location application may be one of multiple location applications caused to be stored in the mobile device by a user of the mobile device to make use of pieces of location information from one or more of its location providers to perform various functions. The trusted location application may employ the location information received from the location provider to present the user with an indication of a location of an item offered (e.g., offered for sale, rent, etc.) within a venue associated with the trusted location application and/or determine an item of interest to the user based on the manner in which the user moves about within the venue. The location provider cooperates with a location network of the venue to analyze characteristics of wireless signals received from one or more wireless network access points (APs) within the venue, and/or other stations (STAs) within the venue, to determine a current location of the mobile device within the venue. The location provider may receive a location almanac from an AP of the location network that specifies locations and/or characteristics of one or more APs of the location network, thereby enabling a relatively high location accuracy level in specifying the current location (e.g., an accuracy within 1 meter). As previously discussed, a location manager may be interposed between the location provider and the trusted location application for the purpose of distributing pieces of location information from one or more location providers to one or more location applications requesting location information. Unfortunately, as also previously discussed, the location manager may be corrupted such that it may not be possible to regard the location manager as trusted. Alternatively or additionally, one of the location applications may be an untrusted location application configured to use the location information associated with the venue to present information concerning items offered at a competing venue to the user in an attempt to induce the user to leave the venue for the competing venue. Trusted communications may be established through the location manager between the location provider and the trusted location application to enable an exchange of the location information therebetween in a manner that does not permit the untrusted location application and/or the location manager itself to receive it and/or to make use of it. As a prelude to establishing such trusted communications, the location provider may employ a combination of credentials received from the trusted location application and/or the location network to verify the trusted location application as trustworthy to receive the location information. Then, one or both of the location provider and the trusted location application may signal the location manager with a request to route the location information only to the trusted location application from the location provider, instead of distributing it to multiple location applications. However, in many mobile devices, the location manager is a component of an operating system (OS) for mobile devices, and it is not uncommon for the integrity of an OS to be compromised (e.g., via a virus, etc.). Thus, the location manager may be deemed to be untrusted resulting in uncertainty as to whether the location manager would honor the request to route the location information only to the trusted location application. To counter the possibility that an untrusted location application associated with a competing venue may still be provided with the location information in spite of such a request made to the location manager, the location provider and the trusted location application may employ encryption in exchanging the location information therebetween. With general reference to notations and nomenclature used herein, portions of the detailed description which follows may be presented in terms of program procedures executed on a computer or network of computers. These procedural descriptions and representations are used by those skilled in the art to most effectively convey the substance of their work to others skilled in the art. A procedure is here, and generally, conceived to be a self-consistent sequence of operations leading to a desired result. These operations are those requiring physical manipulations of physical quantities. Usually, though not necessarily, these quantities take the form of electrical, magnetic or optical signals capable of being stored, transferred, combined, compared, and otherwise manipulated. It proves convenient at times, principally for reasons of common usage, to refer to these signals as bits, values, elements, symbols, characters, terms, numbers, or the like. It should be noted, however, that all of these and similar terms are to be associated with the appropriate physical quantities and are merely convenient labels applied to those quantities. Further, these manipulations are often referred to in terms, such as adding or comparing, which are commonly associated with mental operations performed by a human operator. However, no such capability of a human operator is necessary, or desirable in most cases, in any of the operations described herein that form part of one or more embodiments. Rather, these operations are machine operations. Useful machines for performing operations of various embodiments include general purpose digital computers as selectively activated or configured by a computer program stored within that is written in accordance with the teachings herein, and/or include apparatus specially constructed for the required purpose. Various embodiments also relate to apparatus or systems for performing these operations. These apparatus may be specially constructed for the required purpose or may include a general purpose computer. The required structure for a variety of these machines will be apparent from the description given. Reference is now made to the drawings, wherein like reference numerals are used to refer to like elements throughout. In the following description, for purposes of explanation, numerous specific details are set forth in order to provide a thorough understanding thereof. It may be evident, however, that the novel embodiments can be practiced without these specific details. In other instances, well known structures and devices are shown in block diagram form in order to facilitate a description thereof. The intention is to cover all modifications, equivalents, and alternatives within the scope of the claims. The mobile device 100 may be carried by a user into a venue 409 associated with the location server 300 and in which items are offered (e.g. offered for sale, rent, etc.). In cooperation with one or more access points 494 As depicted, subsets of these computing devices 100, 300, 500 and/or 700 exchange signals associated with determining a current location of the mobile device 100 within the venue 409 through one or both of the networks 499 and 999. However, one or more of these computing devices may exchange other data entirely unrelated to determining a current location of any computing device with each other and/or with still other computing devices (not shown) via one or both of the networks 499 and 999. In various embodiments, the location network 499 may be a wireless network extending within the interior of the venue 409. The network 499 may be configured to adhere to any of a variety of wireless networking specifications including and not limited to one or more of the 802.11 family of specifications promulgated by the Institute of Electrical and Electronics Engineers (IEEE) of New York, N.Y., USA, versions of the Bluetooth® specification promulgated by the Bluetooth® Special Interest Group (Bluetooth SIG) of Kirkland, Wash., USA, version of the Wi-Fi™ specification promulgated by the Wi-Fi™ Alliance of Austin, Tex., USA, and specification under development by the In-Location Alliance of Espoo, Finland. In various embodiments, the network 999 may be a single network possibly limited to extending within a single building or other relatively limited area, a combination of connected networks possibly extending a considerable distance, and/or may include the Internet. Thus, the network 999 may be based on any of a variety (or combination) of communications technologies by which signals may be exchanged, including without limitation, wired technologies employing electrically and/or optically conductive cabling, and wireless technologies employing infrared, radio frequency or other forms of wireless transmission. In various embodiments, the mobile device 100 incorporates one or more of a processor component 150, a storage 160, location providers 170 As will be explained in greater detail, each of the location providers 170 Regardless of the exact manner in which each of the location providers 170 The interface 190 may incorporate circuitry (e.g., demodulators, radio frequency signal amplifiers, etc.) to receive wireless signals employed by one or both of the location providers 170 The location manager 140 incorporates a sequence of instructions operative on the processor component 150 in its role as a main processor component to implement logic to perform various functions. In executing the location manager 140, the processor component 150 receives requests from one or more location applications (e.g., the location applications 110 and 510) for location information indicating a current location of the mobile device 100, and receives location information from one or more location providers (e.g., the location providers 170 In executing the location manager 140, the processor component 550 may also receive from a location application an indication of a location accuracy level required for any location information to be provided to the location application. For example, a location application to present weather forecasts for a current location of the mobile device 100 may require only a relatively low location accuracy such that specifying a current location of the mobile device 100 with an accuracy within one kilometer or several kilometers of its actual current location may be sufficient. However, a location application to present a current location of the mobile device 100 on a street map may require a somewhat greater location accuracy such that an ability to specify a current location of the mobile device 100 with an accuracy within several meters of its actual current location may be necessary. In continuing to execute the location manager 140, the processor component 550 may further receive from a location provider an indication of a location accuracy level able to be provided by the location provider. For example, a location provider employing GPS satellite signals may be able to provide location information with a location accuracy level high enough that a current location of the mobile device 100 may be specified to within a few meters of its actual current location. Such a location accuracy level may be more than sufficient for use in presenting a weather prediction for a current location or presenting an indication of a current location on a street map. However, such a location accuracy level may not be sufficient for use in presenting a current location of the mobile device 100 among rooms, hallways, aisles, etc. of an interior of a venue (e.g., the venue 409). The processor component 550 may selectively distribute location information received from different location providers with different degrees of location accuracy to location applications based on their requested degrees of location accuracy. Further, the processor component 550 may selectively distribute location information received from different location providers to different location applications based on which location provider(s) are able to provide location information at any given time. As familiar to those skilled in the art, different ones of wireless signals from satellites, cellular towers and/or APs of wireless networks may be available at different times in different places. By way of example, entry into a structure (e.g., a house or building) may block receipt of wireless signals from satellites. Each of the location applications 110 and 510 incorporates a sequence of instructions operative on the processor component 150 in its role as a main processor component to implement logic to perform various functions. In executing each of the location applications 110 and 510, the processor component 150 may use location information distributed to each of the location applications 110 and 510 by the location manager 140 to perform a function based on a current location of the mobile device 100 indicated in such location information. To maintain the trusted nature of the trusted location application 510, the processor component 150 may execute the trusted location application 510 in a secure mode and/or with various restrictions in access to a portion of the storage 160 in which the trusted location application 510 is stored (e.g., “sandboxing” or a “secure enclave”). The trusted location application 510 may be associated with the venue 409. In executing the trusted location application 510, the processor component 550 may visually present on the display 180 (e.g., with a visually presented map) an indication of a current location of the mobile device 100 among hallways, rooms, aisles, shelves, kiosks, information desks, restrooms, check-out counters, etc. of the venue 409. The processor component 550 may present information to the user concerning items offered (e.g., offered for sale, rent, etc.) within the venue 409, their location with the venue 409, and/or various promotions (e.g., sales, discounts, coupons, etc.) associated with those items. In executing the trusted location application 510, the processor component 550 may monitor movements of the mobile device 100 (as indicated in the location information it receives) as the user moves about the interior of the venue 409 while carrying the mobile device 100. Instances of the user stopping and/or seeming to linger at specific locations within the venue 409 may be deemed to be indications of the user being interested in one or more items located at those specific locations. In response, the processor component 550 may visually present various promotions associated with those items at those specific locations (e.g., to encourage the user to rent, purchase or otherwise make use of one of those items). The user of the mobile device 100 may obtain the trusted location application 510 from the application server 500. More specifically, the user may have operated the mobile device (e.g., via the controls 120 and the display 180) to access the application server 500 via the network 999, download the trusted location application 510 therefrom, and store it within the storage 160. The user may have chosen to do so due to benefits arising from the convenience of being able to use the trusted location application 510 to find items within the venue 409 and/or to be informed of promotions associated with those items. The untrusted location application 110 may be associated with a competitor of whatever commercial, governmental or non-profit entity may be associated with the venue 409. The user of the mobile device 100 may be a patron of both the venue 409 and a competing venue associated with the competitor, and may therefore choose to download the untrusted location application 110 in addition to trusted location application 510 to make use of benefits offered by the untrusted location application 110 that may be similar to those offered by the trusted location application 510. However, in executing the untrusted location application 110, the processor component 550 may be caused to do more than to simply provide the benefits that induced the user to download the untrusted location application (e.g., being guided through the competing venue). In executing the untrusted location application 110, the processor component 550 may attempt to employ the same location information intended to be employed in execution of the trusted location application 510 by the processor component 550. More specifically, the processor component 550 may be caused by its execution of the untrusted location application 110 to use the location information generated by the location provider 170 In various embodiments, the application server 500 incorporates one or more of a processor component 550, a storage 560, and an interface 590 to couple the application server 500 to at least the network 999. The storage 560 stores one or more of a control routine 540 and the trusted location application 510. Again, the trusted location application 510 may incorporate the credentials 537. The control routine 540 incorporates a sequence of instructions operative on the processor component 550 in its role as a main processor component to implement logic to perform various functions. In executing the control routine 540, the processor component 550 may receive a signal from the mobile device 100 via the network 999 to provide the trusted location application 510 to the mobile device 100. In response, the processor component 550 may so provide the trusted location application to the mobile device 100. The application server 500 may be associated with the entity associated with the venue 409 such that the untrusted location application 110 may have been downloaded from a server unassociated with that entity. Alternatively, the server 500 may be associated with an entirely different entity offering a variety of location applications associated with a variety of different venues for download, including both of the location applications 110 and 510. In various embodiments, the location server 300 incorporates one or more of a processor component 350, a storage 360, and an interface 390 to couple the location server 300 to at least the location network 499. The storage 360 stores one or more of a control routine 340, a location almanac 334, a location data 333 and credentials 337. As previously discussed, the location server 300 is coupled to the APs 494 The control routine 340 incorporates a sequence of instructions operative on the processor component 350 in its role as a main processor component to implement logic to perform various functions. In executing the control routine 340, the processor component 350 may receive a signal from one or more of the APs 494 The location almanac 334 provides indications of locations and/or various characteristics of the APs 494 In determining a current location of the mobile device 100 relative to the APs 494 Returning to Unfortunately, and as previously explained, execution of the location manager 140 by the processor component 150 may result in the location information generated by the location provider 170 In executing the untrusted location application 110, the processor component 550 may employ both the location information intended for the trusted location application 510 and the competing data 133 to disrupt the presentation of information related to items found within the venue 409 with a competing presentation of information related to items at the competing venue. In essence, as the user moves about within the venue 409, competing presentations are made to the user under the control of both of the location applications 510 and 110. In response to indications in their movement of possible interest in an item within the venue 409, both of the location data 333 and the competing data 133 are employed in correlating a location with what the item of interest may be, and competing presentations of promotions associated with that item of interest are made. In essence, the investment in infrastructure made to provide the location network 499 within the venue 409 is used both for and against the entity associated with the venue 409 that made the investment. In an effort to prevent such dueling presentations, one or more location providers of the mobile device 100 (e.g., one or both of the location providers 170 As has been discussed, one or more of the credentials 137, 337 and 537 may be incorporated into one or more of the location providers 170 One or more of the credentials 137, 337 and 537 may be employed in verifying the trustworthiness of at least the trusted location application 510 as a location application that is associated with the venue 409 and/or with the entity associated with the venue. By way of example, the credentials 537 may include a key, and the key may be directly incorporated into the trusted location application 510 or the trusted location application 510 may be digitally signed with the key. Also, the credentials 537 may include a key related to the key of the credentials 537. The location provider 170 As an alternate example, the processor component 350 may itself, through its execution of the control routine 340, perform the verification of the trustworthiness of the trusted location application 510. To maintain the trusted nature of the control routine 340 in performing such verification, the processor component 350 may execute the control routine 340 in a secure mode and/or with various restrictions in access to a portion of the storage 360 in which the control routine 340 is stored (e.g., “sandboxing” or a “secure enclave”). The processor component 350 may request that the location provider 170 The processor component 350 may condition the provision of one or both of the location almanac 334 and the location data 333 to the mobile device 100 on the results of the verification of the trustworthiness of the trusted location application 510. Alternatively or additionally, the location provider 170 In some embodiments, the location providers 170 However, in other embodiments, the processor component 350 of the server 300, in executing the control routine 340, may verify the trustworthiness of one or both of the location providers 170 Upon successful verification of one or both of the location provider 170 Such trusted communications may be established by one or both of the location provider 170 Thus, as an alternative to or in addition to making such a request of the location manager 140, such trusted communications may be established by the location provider 170 However, as also previously discussed, the location manager 140 may be interposed between the location provider 170 As more specifically depicted in As previously discussed, the location provider 170 In various embodiments, each of the processor components 150, 350 and 550 may include any of a wide variety of commercially available processors. Further, one or more of these processor components may include multiple processors, a multi-threaded processor, a multi-core processor (whether the multiple cores coexist on the same or separate dies), and/or a multi-processor architecture of some other variety by which multiple physically separate processors are in some way linked. In various embodiments, each of the storages 160, 360 and 560 may be based on any of a wide variety of information storage technologies, possibly including volatile technologies requiring the uninterrupted provision of electric power, and possibly including technologies entailing the use of machine-readable storage media that may or may not be removable. Thus, each of these storages may include any of a wide variety of types (or combination of types) of storage device, including without limitation, read-only memory (ROM), random-access memory (RAM), dynamic RAM (DRAM), Double-Data-Rate DRAM (DDR-DRAM), synchronous DRAM (SDRAM), static RAM (SRAM), programmable ROM (PROM), erasable programmable ROM (EPROM), electrically erasable programmable ROM (EEPROM), flash memory, polymer memory (e.g., ferroelectric polymer memory), ovonic memory, phase change or ferroelectric memory, silicon-oxide-nitride-oxide-silicon (SONOS) memory, magnetic or optical cards, one or more individual ferromagnetic disk drives, or a plurality of storage devices organized into one or more arrays (e.g., multiple ferromagnetic disk drives organized into a Redundant Array of Independent Disks array, or RAID array). It should be noted that although each of these storages is depicted as a single block, one or more of these may include multiple storage devices that may be based on differing storage technologies. Thus, for example, one or more of each of these depicted storages may represent a combination of an optical drive or flash memory card reader by which programs and/or data may be stored and conveyed on some form of machine-readable storage media, a ferromagnetic disk drive to store programs and/or data locally for a relatively extended period, and one or more volatile solid state memory devices enabling relatively quick access to programs and/or data (e.g., SRAM or DRAM). It should also be noted that each of these storages may be made up of multiple storage components based on identical storage technology, but which may be maintained separately as a result of specialization in use (e.g., some DRAM devices employed as a main storage while other DRAM devices employed as a distinct frame buffer of a graphics controller). In various embodiments, each of the interfaces 190, 390 and 590 may employ any of a wide variety of signaling technologies enabling computing devices to be coupled to other devices as has been described. Each of these interfaces may include circuitry providing at least some of the requisite functionality to enable such coupling. However, each of these interfaces may also be at least partially implemented with sequences of instructions executed by corresponding ones of the processor components (e.g., to implement a protocol stack or other features). Where electrically and/or optically conductive cabling is employed, these interfaces may employ signaling and/or protocols conforming to any of a variety of industry standards, including without limitation, RS-232C, RS-422, USB, Ethernet (IEEE-802.3) or IEEE-1394. Where the use of wireless signal transmission is entailed, these interfaces may employ signaling and/or protocols conforming to any of a variety of industry standards, including without limitation, IEEE 802.11a, 802.11b, 802.11g, 802.16, 802.20 (commonly referred to as “Mobile Broadband Wireless Access”); Bluetooth; ZigBee; or a cellular radiotelephone service such as GSM with General Packet Radio Service (GSM/GPRS), CDMA/1×RTT, Enhanced Data Rates for Global Evolution (EDGE), Evolution Data Only/Optimized (EV-DO), Evolution For Data and Voice (EV-DV), High Speed Downlink Packet Access (HSDPA), High Speed Uplink Packet Access (HSUPA), 4G LTE, etc. Turning more specifically to The control routine 340 may include a verification component 345 to at least assist in verification of a trusted location application of a mobile device (e.g., the trusted location application 510 of the mobile device 100). As has been discussed, the verification component 345 may request credentials of a location provider of a mobile device (e.g., the location provider 170 Turning more specifically to Each of the location providers 170 Turning more specifically to The embodiment of The embodiment of At 2110, a processor component of a location server coupled to a location network providing location services and associated with a venue (e.g., the processor component 350 of the location server 300 coupled to the location network 499 of the venue 409) receives an indication of a mobile device becoming coupled to the location network (e.g., the mobile device 100). As previously discussed, the location network 409 is made up, at least in part, by multiple APs (e.g., the APs 494 At 2120, in response to receipt of the signal, credentials are provided to the mobile device to be used by a portion of its location provider (e.g., the verification component 175 At 2130, the location server receives an indication of the results of the verification of the trusted location application via the location network. If, at 2130, the results indicate that the trusted location application has been verified, then a location almanac and/or location data are transmitted to the mobile device via the location network. As previously explained, the location almanac provides indications of the locations of each AP of the location network in the venue, and one or more characteristics of each AP to effectively “teach” the location provider how to determine the location of the mobile device within the venue. At 2210, a processor component of a mobile device that has become coupled to a location network of a venue (e.g., the processor component 150 or 250 In response to the possibility of the location manager being so compromised, the location information is encrypted at 2260 by the location provider before it is conveyed to the trusted location application through the location manager at 2270. As has been discussed, the key used by the location provider to encrypt the location information may be received from the location network (e.g., provided by a location server associated with the location network). Also, both the key used by the location provider to encrypt the location information may be incorporated into the credentials received from the location network and the key used by the trusted location application to decrypt it may be incorporated into the credentials associated with the trusted location application. At 2310, a processor component of a mobile device that has become coupled to a location network of a venue (e.g., the processor component 150 or 250 At 2330, the mobile device receives the results of the verification of its location provider. If the location provider has been verified at 2340, then the mobile device receives credentials from the location network for use by the location provider in verifying the trustworthiness of a trusted location application associated with the venue of the location network and stored within the mobile device (e.g., the trusted location application 510 stored within the storage 160). At 2360, the credentials of the trusted location application are retrieved for use by the location provider in verifying the trusted location application. At 2370, the credentials received from the location network and retrieved from the trusted location application are used by the location provider to verify the trusted location application. The processing architecture 3000 may include various elements commonly employed in digital processing, including without limitation, one or more processors, multi-core processors, co-processors, memory units, chipsets, controllers, peripherals, interfaces, oscillators, timing devices, video cards, audio cards, multimedia input/output (I/O) components, power supplies, etc. As used in this application, the terms “system” and “component” are intended to refer to an entity of a computing device in which digital processing is carried out, that entity being hardware, a combination of hardware and software, software, or software in execution, examples of which are provided by this depicted exemplary processing architecture. For example, a component can be, but is not limited to being, a process running on a processor component, the processor component itself, a storage device (e.g., a hard disk drive, multiple storage drives in an array, etc.) that may employ an optical and/or magnetic storage medium, an software object, an executable sequence of instructions, a thread of execution, a program, and/or an entire computing device (e.g., an entire computer). By way of illustration, both an application running on a server and the server can be a component. One or more components can reside within a process and/or thread of execution, and a component can be localized on one computing device and/or distributed between two or more computing devices. Further, components may be communicatively coupled to each other by various types of communications media to coordinate operations. The coordination may involve the uni-directional or bi-directional exchange of information. For instance, the components may communicate information in the form of signals communicated over the communications media. The information can be implemented as signals allocated to one or more signal lines. A message (including a command, status, address or data message) may be one of such signals or may be a plurality of such signals, and may be transmitted either serially or substantially in parallel through any of a variety of connections and/or interfaces. As depicted, in implementing the processing architecture 3000, a computing device may include at least a processor component 950, a storage 960, an interface 990 to other devices, and a coupling 955. As will be explained, depending on various aspects of a computing device implementing the processing architecture 3000, including its intended use and/or conditions of use, such a computing device may further include additional components, such as without limitation, a display interface 985. The coupling 955 may include one or more buses, point-to-point interconnects, transceivers, buffers, crosspoint switches, and/or other conductors and/or logic that communicatively couples at least the processor component 950 to the storage 960. Coupling 955 may further couple the processor component 950 to one or more of the interface 990, the audio subsystem 970 and the display interface 985 (depending on which of these and/or other components are also present). With the processor component 950 being so coupled by couplings 955, the processor component 950 is able to perform the various ones of the tasks described at length, above, for whichever one(s) of the aforedescribed computing devices implement the processing architecture 3000. Coupling 955 may be implemented with any of a variety of technologies or combinations of technologies by which signals are optically and/or electrically conveyed. Further, at least portions of couplings 955 may employ timings and/or protocols conforming to any of a wide variety of industry standards, including without limitation, Accelerated Graphics Port (AGP), CardBus, Extended Industry Standard Architecture (E-ISA), Micro Channel Architecture (MCA), NuBus, Peripheral Component Interconnect (Extended) (PCI-X), PCI Express (PCI-E), Personal Computer Memory Card International Association (PCMCIA) bus, HyperTransport™, QuickPath, and the like. As previously discussed, the processor component 950 (corresponding to one or more of the processor components 150 and 350) may include any of a wide variety of commercially available processors, employing any of a wide variety of technologies and implemented with one or more cores physically combined in any of a number of ways. As previously discussed, the storage 960 (corresponding to one or more of the storages 160 and 360) may be made up of one or more distinct storage devices based on any of a wide variety of technologies or combinations of technologies. More specifically, as depicted, the storage 960 may include one or more of a volatile storage 961 (e.g., solid state storage based on one or more forms of RAM technology), a non-volatile storage 962 (e.g., solid state, ferromagnetic or other storage not requiring a constant provision of electric power to preserve their contents), and a removable media storage 963 (e.g., removable disc or solid state memory card storage by which information may be conveyed between computing devices). This depiction of the storage 960 as possibly including multiple distinct types of storage is in recognition of the commonplace use of more than one type of storage device in computing devices in which one type provides relatively rapid reading and writing capabilities enabling more rapid manipulation of data by the processor component 950 (but possibly using a “volatile” technology constantly requiring electric power) while another type provides relatively high density of non-volatile storage (but likely provides relatively slow reading and writing capabilities). Given the often different characteristics of different storage devices employing different technologies, it is also commonplace for such different storage devices to be coupled to other portions of a computing device through different storage controllers coupled to their differing storage devices through different interfaces. By way of example, where the volatile storage 961 is present and is based on RAM technology, the volatile storage 961 may be communicatively coupled to coupling 955 through a storage controller 965 One or the other of the volatile storage 961 or the non-volatile storage 962 may include an article of manufacture in the form of a machine-readable storage media on which a routine including a sequence of instructions executable by the processor component 950 to implement various embodiments may be stored, depending on the technologies on which each is based. By way of example, where the non-volatile storage 962 includes ferromagnetic-based disk drives (e.g., so-called “hard drives”), each such disk drive typically employs one or more rotating platters on which a coating of magnetically responsive particles is deposited and magnetically oriented in various patterns to store information, such as a sequence of instructions, in a manner akin to storage medium such as a floppy diskette. By way of another example, the non-volatile storage 962 may be made up of banks of solid-state storage devices to store information, such as sequences of instructions, in a manner akin to a compact flash card. Again, it is commonplace to employ differing types of storage devices in a computing device at different times to store executable routines and/or data. Thus, a routine including a sequence of instructions to be executed by the processor component 950 to implement various embodiments may initially be stored on the machine-readable storage medium 969, and the removable media storage 963 may be subsequently employed in copying that routine to the non-volatile storage 962 for longer term storage not requiring the continuing presence of the machine-readable storage medium 969 and/or the volatile storage 961 to enable more rapid access by the processor component 950 as that routine is executed. As previously discussed, the interface 990 (possibly corresponding to one or more of the interfaces 190 and 390) may employ any of a variety of signaling technologies corresponding to any of a variety of communications technologies that may be employed to communicatively couple a computing device to one or more other devices. Again, one or both of various forms of wired or wireless signaling may be employed to enable the processor component 950 to interact with input/output devices (e.g., the depicted example keyboard 920 or printer 925) and/or other computing devices, possibly through a network (e.g., the network 999) or an interconnected set of networks. In recognition of the often greatly different character of multiple types of signaling and/or protocols that must often be supported by any one computing device, the interface 990 is depicted as including multiple different interface controllers 995 Where a computing device is communicatively coupled to (or perhaps, actually incorporates) a display (e.g., the depicted example display 980, corresponding to one or more of the displays 180 and 380), such a computing device implementing the processing architecture 3000 may also include the display interface 985. Although more generalized types of interface may be employed in communicatively coupling to a display, the somewhat specialized additional processing often required in visually displaying various forms of content on a display, as well as the somewhat specialized nature of the cabling-based interfaces used, often makes the provision of a distinct display interface desirable. Wired and/or wireless signaling technologies that may be employed by the display interface 985 in a communicative coupling of the display 980 may make use of signaling and/or protocols that conform to any of a variety of industry standards, including without limitation, any of a variety of analog video interfaces, Digital Video Interface (DVI), DisplayPort, etc. More generally, the various elements of the computing devices described and depicted herein may include various hardware elements, software elements, or a combination of both. Examples of hardware elements may include devices, logic devices, components, processors, microprocessors, circuits, processor components, circuit elements (e.g., transistors, resistors, capacitors, inductors, and so forth), integrated circuits, application specific integrated circuits (ASIC), programmable logic devices (PLD), digital signal processors (DSP), field programmable gate array (FPGA), memory units, logic gates, registers, semiconductor device, chips, microchips, chip sets, and so forth. Examples of software elements may include software components, programs, applications, computer programs, application programs, system programs, software development programs, machine programs, operating system software, middleware, firmware, software modules, routines, subroutines, functions, methods, procedures, software interfaces, application program interfaces (API), instruction sets, computing code, computer code, code segments, computer code segments, words, values, symbols, or any combination thereof. However, determining whether an embodiment is implemented using hardware elements and/or software elements may vary in accordance with any number of factors, such as desired computational rate, power levels, heat tolerances, processing cycle budget, input data rates, output data rates, memory resources, data bus speeds and other design or performance constraints, as desired for a given implementation. Some embodiments may be described using the expression “one embodiment” or “an embodiment” along with their derivatives. These terms mean that a particular feature, structure, or characteristic described in connection with the embodiment is included in at least one embodiment. The appearances of the phrase “in one embodiment” in various places in the specification are not necessarily all referring to the same embodiment. Further, some embodiments may be described using the expression “coupled” and “connected” along with their derivatives. These terms are not necessarily intended as synonyms for each other. For example, some embodiments may be described using the terms “connected” and/or “coupled” to indicate that two or more elements are in direct physical or electrical contact with each other. The term “coupled,” however, may also mean that two or more elements are not in direct contact with each other, but yet still co-operate or interact with each other. Furthermore, aspects or elements from different embodiments may be combined. It is emphasized that the Abstract of the Disclosure is provided to allow a reader to quickly ascertain the nature of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. In addition, in the foregoing Detailed Description, it can be seen that various features are grouped together in a single embodiment for the purpose of streamlining the disclosure. This method of disclosure is not to be interpreted as reflecting an intention that the claimed embodiments require more features than are expressly recited in each claim. Rather, as the following claims reflect, inventive subject matter lies in less than all features of a single disclosed embodiment. Thus the following claims are hereby incorporated into the Detailed Description, with each claim standing on its own as a separate embodiment. In the appended claims, the terms “including” and “in which” are used as the plain-English equivalents of the respective terms “comprising” and “wherein,” respectively. Moreover, the terms “first,” “second,” “third,” and so forth, are used merely as labels, and are not intended to impose numerical requirements on their objects. What has been described above includes examples of the disclosed architecture. It is, of course, not possible to describe every conceivable combination of components and/or methodologies, but one of ordinary skill in the art may recognize that many further combinations and permutations are possible. Accordingly, the novel architecture is intended to embrace all such alterations, modifications and variations that fall within the spirit and scope of the appended claims. The detailed disclosure now turns to providing examples that pertain to further embodiments. The examples provided below are not intended to be limiting. In some examples, an apparatus to determine a location may include a processor component and a location provider for execution by the processor component. The location provider may include a location baseband to determine a current location in a venue based on wireless signals received from a location network of the venue, a verification component to verify a trusted location application associated with the venue based on credentials received from the location network and the trusted location application, and an encryption component to encrypt location information indicating the current location and convey the location information to the trusted location application through a location manager interposed between the location provider and the trusted location application based on verification of the trusted location application. Such examples may further include an antenna and an interface coupled to the antenna to receive wireless signals from a location network of a venue, and the baseband may be coupled to the interface. Additionally or alternatively, the location provider may include a location engine to convert raw data generated by the location baseband from the wireless signals and indicative of the current location into the location information. Additionally or alternatively, the apparatus may include an interface to receive the wireless signals, the wireless signals transmitted by a station (STA) of the location network disposed at the venue, the signals conveying the credentials. Additionally or alternatively, the apparatus may include an interface to receive the wireless signals, the wireless signals transmitted by one or more access points (APs) of the location network, the one or more APs disposed about the venue. Additionally or alternatively, the location baseband may receive a location almanac from an AP of the one or more APs, the location almanac indicating locations of the one or more APs within the venue and at least one characteristic of the one or more APs. Additionally or alternatively, the at least one characteristic may include a signal strength of a wireless signal of the wireless signals transmitted by the one or more APs, a time-of-flight, a difference in time of arrival, or an angle of arrival, an angle of departure. Additionally or alternatively, the verification component may receive credentials from an AP of the one or more APs and verify the trusted location application based at least on the credentials received from the trusted location application and the AP. Additionally or alternatively, the apparatus may include the location manager, the location manager may distribute the location information to multiple location applications, and the multiple location applications may include the trusted location application and an untrusted location application. Additionally or alternatively, the location manager may be for execution by the processor component. Additionally or alternatively, the location provider may signal the location manager with a request to convey the location information to no other location application except the trusted location application. Additionally or alternatively, the apparatus may include the trusted location application, and the trusted location application may signal the location manager with a request to convey the location information to no other application except the trusted location application. Additionally or alternatively, the trusted location application may be for execution by the processor component. Additionally or alternatively, the apparatus may include the trusted location application, the trusted location application may provide credentials to the verification component and receive the location information from the location manager, and the trusted location application may include a decryption component to decrypt the location information. Additionally or alternatively, the location network may include multiple APs disposed about the venue, the location provider may receive a location data indicating items offered within the venue and locations of the items within the venue from an AP of the multiple APs, the location provider may convey the location data to the trusted location application, and the trusted location application may include a correlation component to correlate the current location with an item of the items offered within the venue. Additionally or alternatively, the apparatus may include a display and the trusted location application may include a presentation component to visually present a map of the venue and the current location on the map. Additionally or alternatively, the trusted location application may include a presentation component to present an indication of a promotion associated with an item of the items offered within the venue. Additionally or alternatively, the location provider may receive a first key from the location network, and the encryption component to encrypt the location information using the first key. Additionally or alternatively, the apparatus may include the trusted location application, and the trusted location application may receive the location information from the location manager and to decrypt the location information using a second key related to the first key. Additionally or alternatively, the credentials received from the location network may include the first key and the credentials of the trusted location component may include the second key. In some examples, an apparatus to determine a location may include a processor component, an interface to communicatively couple the processor component to a location network of a venue; and a verification component for execution by the processor component to transmit credentials via the location network to a mobile device within the venue, receive from the mobile device an indication of results of verification of a trusted location application of the mobile device using the credentials, and to condition transmission of a location data to the mobile device on the results, the location data indicating items offered within the venue and locations of the items within the venue. Additionally or alternatively, the verification component may condition transmission of a location almanac to the mobile device on the results, the location almanac indicating locations of multiple access points (APs) of the location network disposed about the venue and at least one characteristic of the multiple APs. Additionally or alternatively, the at least one characteristic may include a signal strength of a wireless signal of wireless signals transmitted by the multiple APs. Additionally or alternatively, the apparatus may include a location services component for execution by the processor component to cooperate with multiple access points (APs) of the location network to transmit wireless signals to enable the mobile device to determine a current location of the mobile device within the venue, the multiple APs disposed about the venue. Additionally or alternatively, the verification component may transmit the credentials to an AP of the multiple APs to enable the AP to transmit the credentials to the mobile device. Additionally or alternatively, the credentials may include a first key to enable a location provider of the mobile device to encrypt location information indicating the current location to be conveyed to the trusted location application through a location manager of the mobile device, the first key related to a second key associated with the trusted location application to enable the trusted location application to decrypt the location information. In some examples, a computer-implemented method for determining a location may include determining at a mobile device a current location of the mobile device in a venue based on wireless signals received from a location network of the venue; receiving at the mobile device first credentials from the location network; verifying a trusted location application of the mobile device using the first credentials and second credentials of the trusted location application; and encrypting location information indicating the current location and conveying the location information to the trusted location application through a location manager of the mobile device based on verification of the trusted location application. Additionally or alternatively, the method may include receiving the wireless signals from one or more access points (APs) of the location network, the one or more APs disposed about the venue. Additionally or alternatively, the method may include receiving a location almanac from an AP of the one or more APs, the location almanac indicating locations of the one or more APs within the venue and at least one characteristic of the one or more APs. Additionally or alternatively, the at least one characteristic may include a signal strength of a wireless signal of the wireless signals transmitted by the one or more APs. Additionally or alternatively, the method may include receiving the first credentials from an AP of the one or more APs. Additionally or alternatively, the location manager may distribute the location information to multiple location applications, and the multiple location applications may include the trusted location application and an untrusted location application. Additionally or alternatively, the method may include signaling the location manager with a request to convey the location information to no other location application except the trusted location application. Additionally or alternatively, the method may include receiving the second credentials from the trusted location application, and decrypting the location information at the trusted location application. Additionally or alternatively, the location network may include multiple APs disposed about the venue; and the method may include receiving a location data indicating items offered within the venue and locations of the items within the venue from an AP of the multiple APs, conveying the location data to the trusted location application, and correlating at the trusted location application the current location with an item of the items offered within the venue. Additionally or alternatively, the method may include visually presenting a map of the venue and the current location on the map. Additionally or alternatively, the method may include presenting an indication of a promotion associated with an item of the items offered within the venue. Additionally or alternatively, the method may include receiving a first key from the location network and encrypting the location information using the first key. Additionally or alternatively, the method may include decrypting the location information using a second key related to the first key. Additionally or alternatively, the first credentials may include the first key and the second credentials may include the second key. In some examples, at least one machine-readable storage medium may include instructions that when executed by a computing device, cause the computing device to determine at a mobile device a current location of the mobile device in a venue based on wireless signals received from a location network of the venue, receive at the mobile device first credentials from the location network, verify a trusted location application of the mobile device using the first credentials and second credentials of the trusted location application, and encrypt location information indicating the current location and convey the location information to the trusted location application through a location manager of the mobile device based on verification of the trusted location application. Additionally or alternatively, the computing device may be caused to receive the wireless signals from one or more access points (APs) of the location network, the one or more APs disposed about the venue. Additionally or alternatively, the computing device may be caused to receive a location almanac from an AP of the one or more APs, the location almanac indicating locations of the one or more APs within the venue and at least one characteristic of the one or more APs. Additionally or alternatively, the at least one characteristic may include a signal strength of a wireless signal of the wireless signals transmitted by the one or more APs. Additionally or alternatively, the computing device may be caused to receive the first credentials from an AP of the one or more APs. Additionally or alternatively, the location manager may distribute the location information to multiple location applications, and the multiple location applications may include the trusted location application and an untrusted location application. Additionally or alternatively, the computing device may be caused to signal the location manager with a request to convey the location information to no other location application except the trusted location application. Additionally or alternatively, the computing device may be caused to receive the second credentials from the trusted location application, and decrypt the location information at the trusted location application. Additionally or alternatively, the computing device may be caused to receive a location data indicating items offered within the venue and locations of the items within the venue from an AP of multiple APs of the location network, convey the location data to the trusted location application, and correlate at the trusted location application the current location with an item of the items offered within the venue. Additionally or alternatively, the computing device may be caused to visually present a map of the venue and the current location on the map. Additionally or alternatively, the computing device may be caused to present an indication of a promotion associated with an item of the items offered within the venue. Additionally or alternatively, the computing device may be caused to receive a first key from the location network, and encrypt the location information using the first key. Additionally or alternatively, the computing device may be caused to decrypt the location information using a second key related to the first key. Additionally or alternatively, the first credentials may include the first key and the second credentials may include the second key. In some examples, at least one machine-readable storage medium may include instructions that when executed by a computing device, cause the computing device to perform any of the above. In some examples, an apparatus to assign processor component cores to perform task portions may include means for performing any of the above. Various embodiments are generally directed to techniques for conveying location information between a location provider and a trusted location application within a mobile device through trusted communications to preclude its provision to an untrusted location application. An apparatus includes a processor component; and a location provider for execution by the processor component comprising a location baseband to determine a current location in a venue based on wireless signals received from a location network of the venue, a verification component to verify a trusted location application associated with the venue based at least on credentials received from the trusted location application, and an encryption component to encrypt location information indicating the current location and convey the location information to the trusted location application through a location manager interposed between the location provider and the trusted location application based on verification of the trusted location application. Other embodiments are described and claimed. 1. An apparatus to determine a location comprising:
a processor component; and a location provider for execution by the processor component comprising:
a location baseband to determine a current location in a venue based on wireless signals received from a location network of the venue; a verification component to verify a trusted location application associated with the venue based on credentials received from the location network and the trusted location application; and an encryption component to encrypt location information indicating the current location and convey the location information to the trusted location application through a location manager interposed between the location provider and the trusted location application based on verification of the trusted location application. 2. The apparatus of 3. The apparatus of 4. The apparatus of 5. The apparatus of 6. The apparatus of 7. The apparatus of 8. The apparatus of 9. The apparatus of 10. The apparatus of 11. The apparatus of 12. The apparatus of 13. An apparatus to determine a location comprising:
an antenna; an interface coupled to the antenna to receive wireless signals from a location network of a venue; a processor component; and a location provider for execution by the processor component comprising:
a location baseband coupled to the interface to determine a current location in the venue based on the wireless signals; a verification component to verify a trusted location application associated with the venue based on credentials received from the location network and the trusted location application; and an encryption component to encrypt location information indicating the current location and convey the location information to the trusted location application through a location manager interposed between the location provider and the trusted location application based on verification of the trusted location application. 14. The apparatus of 15. The apparatus of 16. A computing-implemented method for determining a location comprising:
determining at a mobile device a current location of the mobile device in a venue based on wireless signals received from a location network of the venue; receiving at the mobile device first credentials from the location network; verifying a trusted location application of the mobile device using the first credentials and second credentials of the trusted location application; and encrypting location information indicating the current location and conveying the location information to the trusted location application through a location manager of the mobile device based on verification of the trusted location application. 17. The computer-implemented method of 18. The computer-implemented method of 19. The computer-implemented method of 20. The computer-implemented method of 21. The computer-implemented method of 22. The computer-implemented method of receiving the second credentials from the trusted location application; and decrypting the location information at the trusted location application. 23. The computer-implemented method of receiving a location data indicating items offered within the venue and locations of the items within the venue from an AP of the multiple APs; conveying the location data to the trusted location application; and correlating at the trusted location application the current location with an item of the items offered within the venue. 24. The computer-implemented method of 25. At least one machine-readable storage medium comprising instructions that when executed by a computing device, cause the computing device to perform the method of any of CROSS-REFERENCE TO RELATED APPLICATIONS
TECHNICAL FIELD
BACKGROUND
BRIEF DESCRIPTION OF THE DRAWINGS
DETAILED DESCRIPTION